LastPass is alerting its users to a malicious campaign employing the CryptoChameleon phishing kit, notorious for cryptocurrency theft. Researchers have identified CryptoChameleon as a sophisticated phishing kit initially used against Federal Communications Commission (FCC) employees through counterfeit Okta single sign-on (SSO) pages.
Security experts at Lookout have found that this phishing kit has also compromised major cryptocurrency platforms such as Binance, Coinbase, Kraken, and Gemini by mimicking login pages for services like Okta, Gmail, iCloud, Outlook, Twitter, Yahoo, and AOL.
In recent investigations, LastPass has uncovered that attackers have integrated their service into the CryptoChameleon kit, setting up a fraudulent phishing site at “help-lastpass[.]com.”
The attackers employ a range of social engineering tactics, including voice phishing, where they contact victims pretending to be LastPass employees assisting with account security after purported unauthorized access. Here’s how the scam typically unfolds:
- Victims receive a call from an 888 number about unauthorized access to their LastPass account, urging them to press “1” to block access or “2” to allow it.
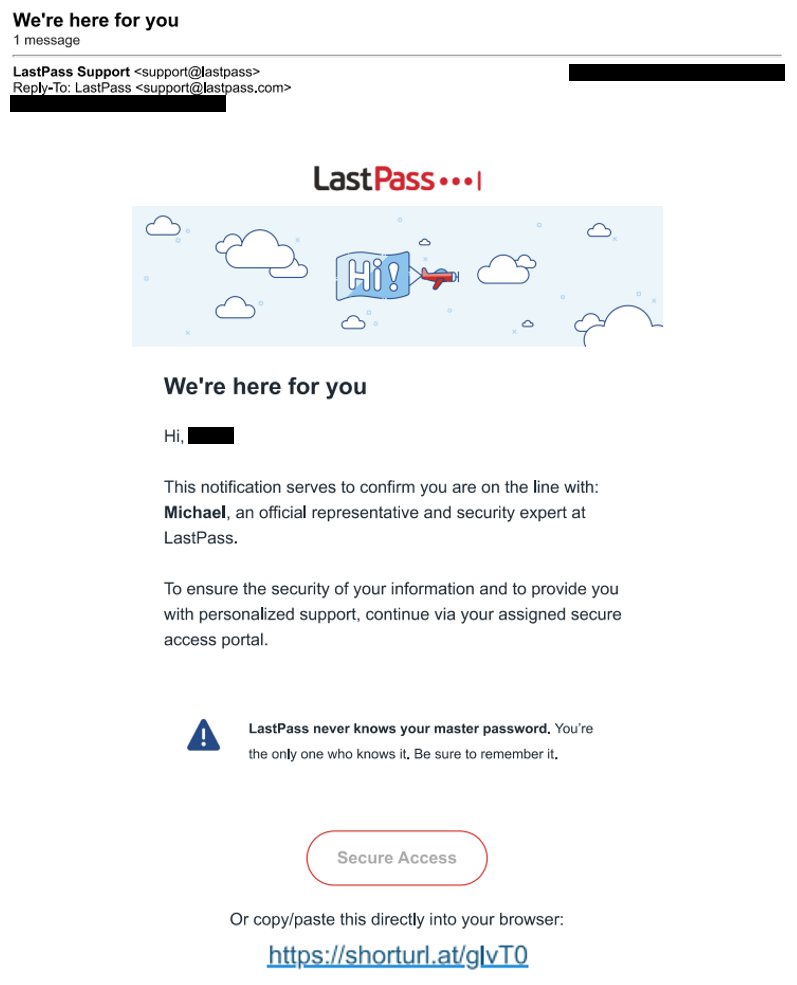
- If the victim attempts to block the access, they receive a follow-up call from a spoofed number. The caller, posing as a LastPass support agent, sends a phishing email from “support@lastpass” containing a link to the deceptive site.
- Upon entering their master password on the fake site, the attacker gains the ability to alter account settings and lock out the legitimate user.
- Actual phishing site: “help-lastpass[.]com”
- Shortened URL Embedded in Email: shorturl[.]at/glvT0
- Phishing Email Subject Line: We’re here for you
- Spoofed Sender: Shows as LastPass Support <support@lastpass>
Although the malicious website is currently offline, the likelihood of similar future campaigns remains high, with criminals likely to employ new domains.
LastPass advises users to remain cautious against suspicious phone calls, messages, or emails claiming to represent LastPass and demanding immediate action. Warning signs of this campaign include emails titled “We’re here for you” and links shortened via URL services. Users should report any dubious communications to abuse@lastpass.com.
It is crucial to keep your master password confidential, as it is the gateway to all your sensitive information.