In a significant cybersecurity development, researchers at Lookout have uncovered a sophisticated phishing kit dubbed CryptoChameleon. This new threat imitates the login pages of prominent cryptocurrency services, aiming its sights primarily at mobile device users. The phishing kit is adept at creating indistinguishable replicas of single sign-on (SSO) pages. By leveraging email, SMS, and voice phishing tactics, attackers deceive individuals into divulging sensitive information. This includes usernames, passwords, password reset URLs, and even photo IDs, with hundreds of victims already reported, predominantly within the United States.
The Scope of CryptoChameleon’s Impact
Cybersecurity experts at Lookout have detailed how CryptoChameleon has ensnared employees from the Federal Communications Commission (FCC) and users of major cryptocurrency platforms such as Binance, Coinbase, Gemini, Kraken, ShakePay, Caleb & Brown, and Trezor. To date, over 100 individuals have fallen prey to these meticulously crafted phishing attacks.
Sophisticated Tactics to Evade Detection
A notable aspect of the CryptoChameleon phishing kit is its use of CAPTCHA tests. Victims are presented with a fake login screen only after completing a CAPTCHA, effectively bypassing automated analysis tools. Moreover, attackers distribute these phishing pages through unsolicited phone calls and text messages. They impersonate customer support teams, falsely claiming to secure accounts following a supposed hack.
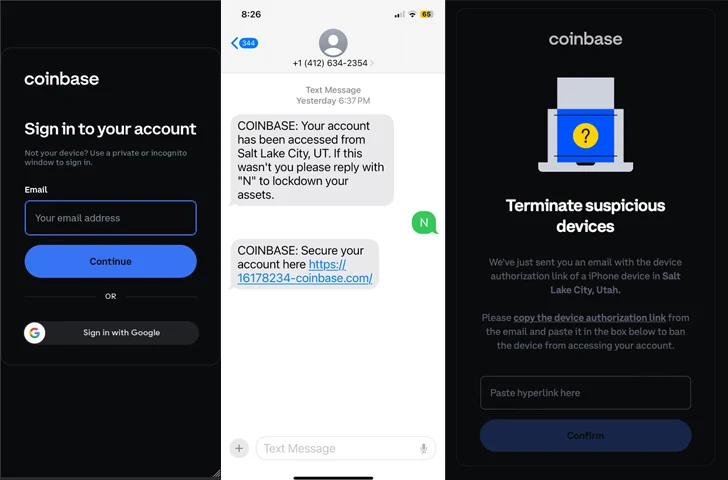
The Real-Time Theft of Credentials
Once victims enter their credentials, they may be prompted to provide a two-factor authentication (2FA) code or asked to wait while their information is purportedly verified. Attackers attempt to log in with these credentials in real-time, redirecting victims based on the additional information requested by the multi-factor authentication service. The phishing kit enhances its illusion of legitimacy by allowing operators to customize the phishing page in real-time. This includes displaying the last two digits of the victim’s actual phone number and choosing the length of the token requested. The one-time password entered by the user is captured by the attacker, facilitating unauthorized access to online services.
Lookout’s analysis draws parallels between CryptoChameleon and tactics used by Scattered Spider, especially in impersonating Okta and using domains previously associated with the group. Despite these similarities, the phishing kit displays unique capabilities and control infrastructure, indicating possible copycat behavior among cybercriminal groups.
The Uncertain Origins of CryptoChameleon
The origins of CryptoChameleon remain unclear, raising questions about whether it is the work of a single threat actor or a shared tool among various groups. The phishing kit’s success lies in its high-quality phishing URLs, the authenticity of the login pages, the creation of a sense of urgency, and consistent communication through SMS and voice calls.
Staying Ahead of Cyber Threats
To protect yourself from phishing attacks, consider these proactive steps:
- Be Skeptical of Unsolicited Communications: Treat emails, SMS, and voice calls with caution, especially if they request personal information or direct you to log in to an account.
- Verify Contact Origins: If unsure about the legitimacy of a communication, contact the organization directly using official channels to verify its authenticity.
- Use Multi-Factor Authentication (MFA): Enable MFA on all accounts that offer it to add an extra layer of security, making it more difficult for attackers to gain unauthorized access.
- Keep Software and Systems Updated: Regularly update your operating system, browser, and all applications to protect against vulnerabilities that could be exploited by phishers.
- Educate Yourself on Phishing Techniques: Familiarize yourself with the latest phishing tactics to better recognize and avoid them.
- Check URLs Carefully: Hover over links to see the actual URL before clicking. Ensure the website is secure (https) and the domain name is spelled correctly.
- Use Strong, Unique Passwords: Create complex passwords that are difficult to guess and use a different password for each account.
- Backup Important Data: Regularly back up important data to an external drive or cloud storage to prevent loss in case of a phishing attack leading to ransomware.
- Be Wary of Too-Good-To-Be-True Offers: Phishers often lure victims with offers that seem too good to be true. Approach such offers with skepticism.
- Report Phishing Attempts: Report suspected phishing emails to your email provider and phishing attempts to the appropriate authorities or organizations.
By adopting these practices, individuals can significantly enhance their defenses against phishing attacks and protect their personal and financial information from cybercriminals.
About Purple Shield Security
Purple Shield Security isn’t just another cyber security firm. Think of us as your digital world’s protectors, always ready to keep your business safe from the latest cyber threats. Our team is full of passionate experts who do more than just look after your data and systems; we give you peace of mind. We offer a wide range of services like Managed Cyber Security, Cyber Security Consulting, Cyber Security Risk Analysis, Cyber Defense Services, Cyber Security Incident Response, and vCISO.
Don’t put off making your business safer. Contact us now to see how Purple Shield Security can upgrade your cyber defenses.

