Many businesses in Los Angeles are operating without a clear understanding of their cybersecurity exposure. Threats continue to grow more sophisticated, but most organizations don’t realize how vulnerable they are until it’s too late.
Every new SaaS account, firewall rule, or vendor integration adds another path into your business. A successful attack doesn’t just impact IT systems—it can disrupt operations, erode customer trust, and lead to financial and legal consequences.
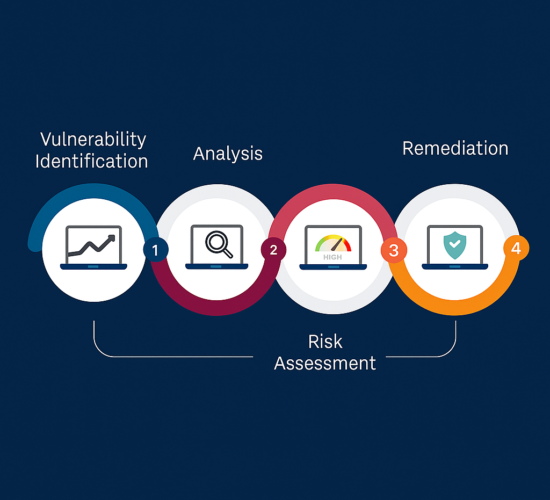
At Purple Shield Security, we help business owners, executives, and leadership teams take a proactive approach. Our vulnerability and risk assessment service is designed to uncover weaknesses before they’re exploited and give you a clear picture of where you stand. We don’t rely on assumptions or generic checklists. Every assessment is tailored to your specific environment, risk profile, and regulatory obligations.
Why a Structured Assessment Matters
- Reveals your true risk profile—using evidence, not industry guesswork.
- Channels budget to the biggest pay-offs by ranking gaps on business impact and remediation effort.
- Builds one set of artefacts for auditors and insurers by mapping findings to NIST 800-53, CIS 18, HIPAA, HITRUST, and PCI-DSS in a single project.
- Hardens both cloud and on-premise environments—the most common footholds attackers exploit across organisations in Los Angeles.
- Speeds up detection and response by supplying incident-ready playbooks tied to each critical weakness.
- Creates a measurable security baseline so you can track year-over-year improvement and prove ROI to the board.
- Strengthens your hand with cyber-insurance carriers by documenting due diligence and risk-reduction steps.
- Aligns executives and engineers by translating technical findings into plain-language business outcomes.