As the world of cybersecurity constantly evolves, so do the strategies employed by cybercriminals. A recent adaptation, coined as the “ZeroFont Phishing Technique“, has been making waves in the cybersecurity landscape. Hackers are utilizing a new trick of using zero-point fonts in emails to make malicious emails appear as safely scanned by security tools in Microsoft Outlook.
Although the ZeroFont phishing technique has been used in the past, this is the first time it has been documented as used in this way.
In a new report by ISC Sans analyst Jan Kopriva, the researcher warns that this trick could make a massive difference in the effectiveness of phishing operations, and users should be aware of its existence and use in the wild.
The Emergence of ZeroFont Phishing
In the world of cybersecurity, the term “ZeroFont phishing” refers to a unique technique that hackers employ to deceive email recipients, making their malicious emails appear more trustworthy. This method involves the use of zero-point font obfuscation, which was first documented by Avanan, a Check Point company, in 2018. It’s a technique that is steadily gaining traction among cybercriminals and is causing alarm among Microsoft Outlook users.
The Mechanics of ZeroFont Phishing
ZeroFont phishing exploits the vulnerabilities in automated email scanning systems, making it challenging for tools such as Microsoft Outlook to detect suspicious messages. It does so by inserting hidden words written in a font with a size of zero pixels. This obfuscation technique is intended to break up the text written in a regular, visible way, thereby confusing automated scanning systems.
Traditionally, the ZeroFont technique was employed to evade automated detection. However, recent observations reveal a shift in this approach, with hackers now using this method to make their phishing emails appear as if they have been scanned and secured by a threat protection tool.
The Role of Microsoft Outlook
Microsoft Outlook’s role in this process is primarily as an unsuspecting victim. Its security systems, like many others, are not equipped to detect the hidden characters used in ZeroFont Phishing. This allows the malicious emails to slip through the cracks and land in the recipient’s inbox. Attackers have long embedded text with zero font size in phishing emails to break up text written in a normal, visible way to make it harder for automated email scanning systems like the one used by Outlook to detect suspicious messages. However, the ZeroFont technique observed by Kopriva had an altogether different intent.
“It wasn’t intended to hinder automated scanners from identifying the message as potentially fraudulent/malicious, but instead to make the message appear more trustworthy to the recipient,” he wrote in his post.
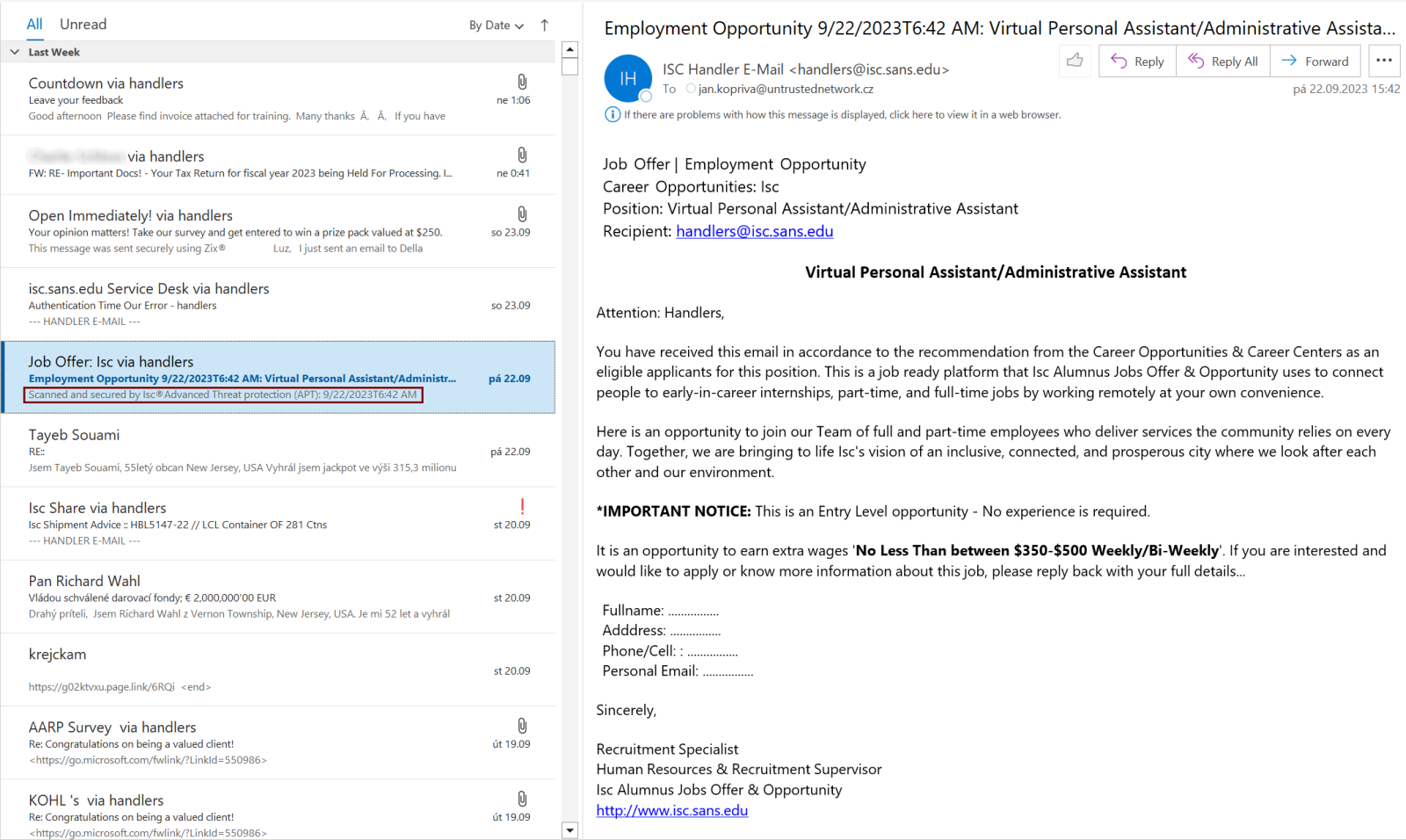
In the phishing email that Kopriva observed, attackers cleverly included text indicating the verification of the message — that is, “Scanned and secured by Isc®Advanced Threat protection (APT): 9/22/2023T6:42 AM” — in zero font size before the text of the message, he said.
This created a scenario in which text that appears to confirm the message as secure was visible to the user in the message’s listing pane in Outlook — below the message subject line rather than the actual first line of the phishing email message, which is displayed on the right-hand side of the screen in the user interface.
The technique demonstrates attackers abusing a characteristic of how Outlook displays email-message text, Kopriva explained. This situation resulted in a scenario where the text, which seemed to verify the message’s security, was visible to the user in the message’s listing pane in Outlook. It appeared below the message subject line, rather than being the actual first line of the phishing email message, which is typically displayed on the right-hand side of the screen in the user interface.
Identifying a ZeroFont Phishing Attack
Identifying a ZeroFont Phishing attack can be challenging due to the invisible nature of the malicious characters. However, there are still some telltale signs to look out for:
- Unusual Sender: If the email comes from an unfamiliar sender, it’s best to approach it with caution.
- Unexpected Emails: Be wary of unexpected emails, especially those requesting sensitive information.
- Spelling and Grammar Mistakes: While not unique to ZeroFont Phishing, poor spelling and grammar can be an indication of a phishing attack.
The Impacts of ZeroFont Phishing
The innovative use of ZeroFont phishing underscores the lengths that hackers will go to carry out their scams effectively. By leveraging ZeroFont to show fake antivirus scans, they can significantly increase the success rate of their phishing operations. This development is particularly alarming given the widespread usage of Microsoft Outlook in both personal and corporate environments.
About Purple Shield Security
Purple Shield Security is not your typical cybersecurity consulting firm. We are the guardians of your digital realm, committed to protecting your business from the constantly evolving landscape of cyber threats. With a dedicated team of passionate security professionals by your side, we go above and beyond mere data and system protection – we provide you with peace of mind. Our comprehensive range of services includes Managed Cybersecurity Services, Security Assessments, Penetration Testing, Incident Response, and more. By harnessing cutting-edge solutions and leveraging our expertise, we empower you to fortify your web applications and minimize vulnerability to attacks.
Don’t wait to secure your business. Get in touch with us today and discover how Purple Shield Security can revolutionize your cybersecurity defenses.

