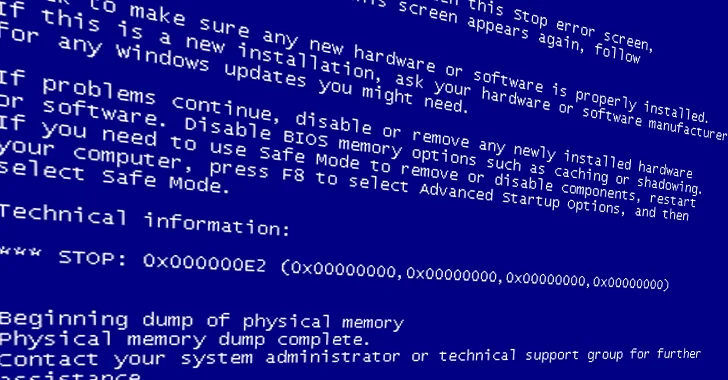
Security experts have recently uncovered a significant number of vulnerable Windows Driver Model (WDM) and Windows Driver Frameworks (WDF) drivers, raising concerns about their potential exploitation by threat actors. This discovery reveals a severe risk in the digital landscape, as attackers, even without privileged access, could exploit these vulnerabilities to seize complete control of devices and execute unauthorized code on affected systems. The scope of this threat encompasses as many as 34 unique vulnerable drivers, amplifying the urgency for robust cybersecurity measures.
Takahiro Haruyama, a distinguished senior threat researcher at VMware Carbon Black, played a pivotal role in drawing attention to the gravity of this vulnerability. He sounded the alarm by highlighting the potential for attackers to tamper with firmware and elevate their privileges within the operating system, setting the stage for potentially devastating breaches. This finding builds upon previous investigations, such as the Symbolic Execution-driven ScrewedDrivers and POPKORN projects, which aimed to streamline the identification of vulnerable drivers, fortifying our understanding of this pressing issue.
The research primarily centered on drivers facilitating firmware access through port I/O and memory-mapped I/O. Among the roster of 34 identified vulnerable drivers are AODDriver.sys, ComputerZ.sys, dellbios.sys, GEDevDrv.sys, GtcKmdfBs.sys, IoAccess.sys, kerneld.amd64, ngiodriver.sys, nvoclock.sys, PDFWKRNL.sys (CVE-2023-20598), RadHwMgr.sys, rtif.sys, rtport.sys, stdcdrv64.sys, and TdkLib64.sys (CVE-2023-35841). Moreover, out of this selection, six drivers provide access to kernel memory, empowering attackers to elevate their privileges and evade security solutions. An additional 12 drivers possess the potential to undermine security mechanisms, including the vital kernel address space layout randomization (KASLR).
A matter of particular concern is the revelation that seven of these drivers, including Intel’s stdcdrv64.sys, can be utilized to erase firmware stored in the SPI flash memory. This potent capability renders the system unbootable, a grave consequence. Fortunately, Intel has proactively addressed this issue by releasing a fix, offering some respite in the face of this threat. To exacerbate the situation, specific Windows Driver Framework (WDF) drivers, such as WDTKernel.sys and H2OFFT64.sys, though not inherently vulnerable in terms of access control, can be easily weaponized by privileged threat actors to launch a Bring Your Own Vulnerable Driver (BYOVD) attack. This technique has already been observed in the activities of various malicious groups, including the North Korea-linked Lazarus Group. Attackers employ BYOVD attacks to gain elevated privileges, disable security software on compromised endpoints, and successfully evade detection.
While the current research predominantly emphasizes firmware access, Haruyama emphasizes the potential for extending the analysis to cover a wider array of attack vectors, including the termination of arbitrary processes. This underscores the perpetual nature of driver vulnerability as an ever-present concern, demanding ongoing vigilance and adaptation in the realm of cybersecurity.
In summary, the discovery of these vulnerable Windows drivers serves as a stern reminder of the evolving threats in the digital sphere. Continuous efforts are crucial to mitigate these vulnerabilities and stay ahead of potential attackers in this dynamic cybersecurity landscape.
About Purple Shield Security
Purple Shield Security is not your typical cybersecurity consulting firm. We are the guardians of your digital realm, committed to protecting your business from the constantly evolving landscape of cyber threats. With a dedicated team of passionate security professionals by your side, we go above and beyond mere data and system protection – we provide you with peace of mind. Our comprehensive range of services includes Managed Cybersecurity Services, Security Assessments, Penetration Testing, Incident Response, and more. By harnessing cutting-edge solutions and leveraging our expertise, we empower you to fortify your web applications and minimize vulnerability to attacks.
Don’t wait to secure your business. Get in touch with us today and discover how Purple Shield Security can revolutionize your cybersecurity defenses.
#cybersecuritynews #securitynews #hacking #datasecurity #windows #microsoft #softwarevulnerability #applicationvulnerability