In the evolving landscape of cyber security, a sophisticated phishing-as-a-service (PhaaS) platform, Tycoon 2FA, is posing significant threats to Microsoft 365 and Gmail accounts, effectively bypassing two-factor authentication (2FA) mechanisms. Discovered by Sekoia analysts in October 2023, Tycoon 2FA has been making waves in the cybercriminal community since August 2023, targeting unsuspecting users through advanced phishing attacks.
Understanding Tycoon 2FA’s Modus Operandi
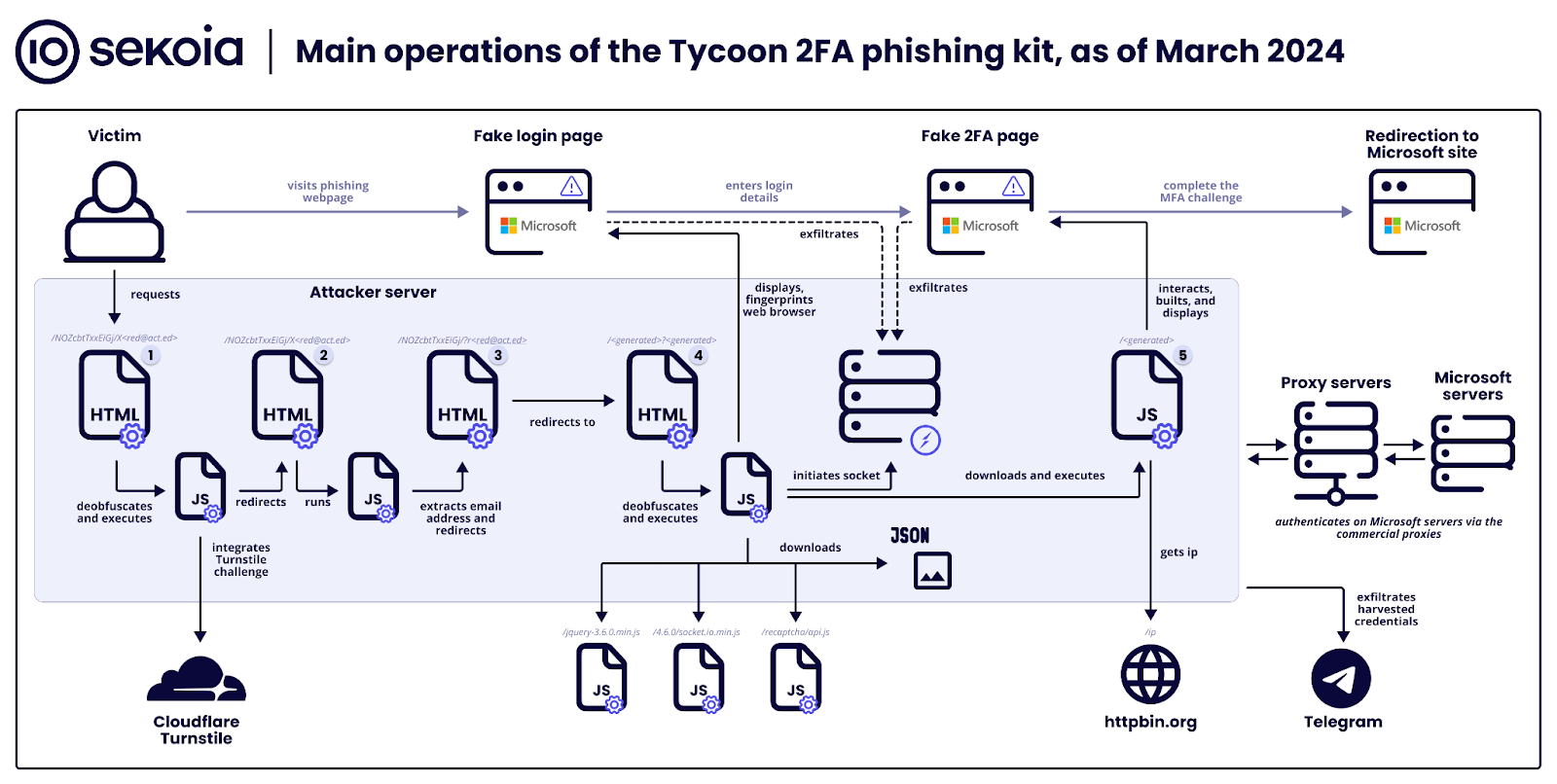
The Tycoon 2FA platform employs a highly sophisticated multi-step process to deceive users and steal sensitive information. By setting up a reverse proxy server, the attackers capture session cookies during a successful MFA challenge, allowing them unauthorized access to user accounts. This process is meticulously designed to trick victims into providing their credentials, ultimately bypassing multi-factor authentication safeguards.
The Phishing Attack Lifecycle
Sekoia’s detailed analysis outlines the phishing attack in seven distinct stages, from the initial distribution of malicious links to the final redirection to a seemingly legitimate page. This methodical approach underscores the high level of sophistication involved in Tycoon 2FA’s operations, highlighting the importance of caution among internet users.
- Stage 0 – Attackers distribute malicious links via emails with embedded URLs or QR codes, tricking victims into accessing phishing pages.
- Stage 1 – A security challenge (Cloudflare Turnstile) filters out bots, allowing only human interactions to proceed to the deceptive phishing site.
- Stage 2 – Background scripts extract the victim’s email from the URL to customize the phishing attack.
- Stage 3 – Users are quietly redirected to another part of the phishing site, moving them closer to the fake login page.
- Stage 4 – This stage presents a fake Microsoft login page to steal credentials, using WebSockets for data exfiltration.
- Stage 5 – The kit mimics a 2FA challenge, intercepting the 2FA token or response to bypass security measures.
- Stage 6 – Finally, victims are directed to a legitimate-looking page, obscuring the phishing attack’s success.
Evolution and Sophistication of Tycoon 2FA
The latest version of Tycoon 2FA introduces several significant enhancements aimed at increasing the stealth and efficacy of phishing attacks. These include updates to JavaScript and HTML code, advanced filtering mechanisms to evade detection, and the use of pseudorandom names for URLs to conceal malicious activities. Such advancements indicate a relentless pursuit of innovation among cybercriminals.
The Scale of Tycoon 2FA’s Operations
The extensive use of Tycoon 2FA by cybercriminals is evident in the substantial number of transactions recorded in the linked Bitcoin wallet since the platform’s launch in August 2023. With over 530 transactions exceeding the entry price for a 10-day phishing link, the financial impact of Tycoon 2FA’s activities is significant, emphasizing the lucrative nature of phishing-as-a-service platforms.
Protecting Against Phishing Attacks
As Tycoon 2FA and similar PhaaS platforms continue to evolve, it’s crucial for individuals and organizations to adopt comprehensive cyber security measures. This includes staying informed about the latest phishing tactics, implementing advanced security protocols, and fostering a culture of cyber awareness.
About Purple Shield Security
Purple Shield Security stands out from the crowd of cyber security firms. Picture us as the guardians of your digital space, always on the lookout to protect your business from the newest cyber dangers. Our team isn’t just made up of experts who care for your data and systems; they’re passionate about giving you a sense of security. We’ve got a variety of services to help keep you safe, including Managed Cyber Security, Cyber Security Consulting, Risk Analysis, Defense Services, Incident Response, and even a virtual Chief Information Security Officer (vCISO).
Don’t put off making your business safer. Contact us now to see how Purple Shield Security can upgrade your cyber defenses.