In February 2024, EclecticIQ cybersecurity researchers discovered phishing campaigns targeting financial institutions using embedded QR codes in PDF attachments to redirect victims to phishing URLs. Recently, these campaigns have begun using a Phishing-as-a-Service (PhaaS) platform known as ONNX Store, which now targets both Microsoft 365 and Office 365 email accounts. The platform enables phishing attacks through an easy-to-use interface provided by Telegram bots.
ONNX Store Overview
ONNX Store, a sophisticated phishing platform, provides tools for launching phishing campaigns, including a two-factor authentication (2FA) bypass mechanism. This feature allows attackers to intercept 2FA tokens, increasing the success rate of business email compromise (BEC) attacks. The phishing pages mimic genuine Microsoft 365 login interfaces, tricking victims into entering their authentication details. Analysts believe ONNX Store is a rebranded version of the Caffeine phishing kit, previously discovered by Mandiant in 2022, due to similarities in infrastructure and advertising methods on Telegram channels.
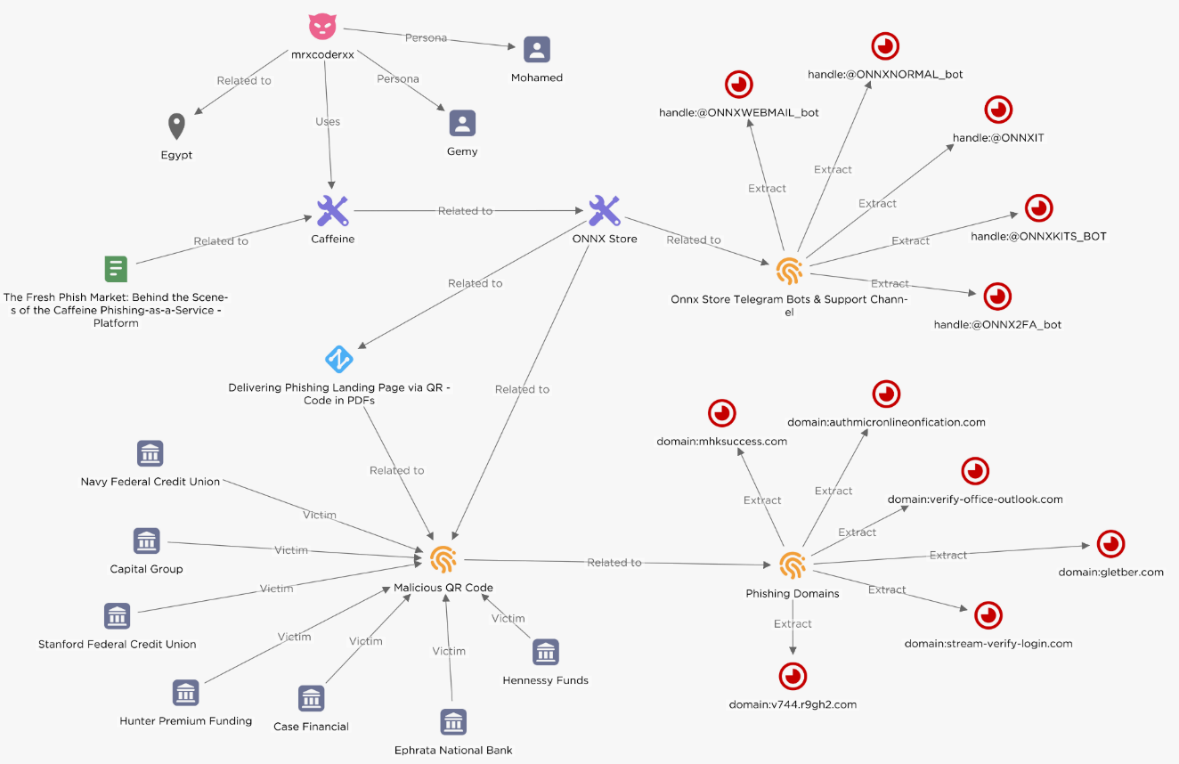
Operational Details
ONNX Store employs several Telegram bots to manage operations:
- @ONNXIT: Manages client support.
- @ONNX2FA_bot: Receives 2FA codes from successful phishing operations.
- @ONNXNORMAL_bot: Receives Microsoft Office 365 login credentials.
- @ONNXWEBMAIL_bot: Controls a webmail server for sending phishing emails.
- @ONNXKITS_BOT: Manages payments and order tracking for ONNX Store services.
Features and Services
ONNX Store offers various subscription tiers:
- Webmail Normal ($150/month): Customizable phishing pages and webmail server.
- Office Normal ($200/month): Email credential harvesting capabilities without bypassing 2FA.
- Office Redirect ($200/month): Creates “Fully Undetectable (FUD)” links using trusted domains for redirection.
- Office 2FA Cookie Stealer ($400/month): Captures 2FA tokens and cookies, featuring country blocking and email grabbing.
The platform uses encrypted JavaScript code that decrypts during page load, adding a layer of obfuscation to evade detection by anti-phishing tools. Additionally, ONNX leverages Cloudflare services to prevent domain takedowns, using CAPTCHA and IP proxying to shield its malicious activities.
Attack Mechanisms
ONNX Store uses embedded QR codes in PDF attachments, a technique known as “quishing,” to distribute phishing URLs. These QR codes are scanned by mobile devices, bypassing endpoint detection systems on organizational networks. Once scanned, the QR codes direct victims to phishing pages that capture login credentials and 2FA tokens in real-time, enabling attackers to hijack accounts before the tokens expire.
Infrastructure and Security Measures
ONNX Store utilizes bulletproof hosting services to ensure uninterrupted operations despite reports and takedowns. These services, advertised with slogans like “Everything is allowed” and “Ignore all abuse reports,” provide a haven for cybercriminals. ONNX Store’s infrastructure shows similarities in domain registrants and SSL issuers, primarily using Google Trust Services LLC and domains registered through NameSilo and EVILEMPIRE-AS.
Broader Impact and Mitigation Strategies
Phishing toolkits like ONNX Store pose a significant threat by enabling cybercriminals to launch effective phishing campaigns. Stolen credentials are often sold on underground forums and used by ransomware groups as an initial compromise vector. To combat these threats, organizations should implement comprehensive prevention strategies, such as:
- Blocking PDF and HTML attachments from unverified sources.
- Restricting access to HTTPS websites with untrusted or expired certificates.
- Deploying FIDO2 hardware security keys for high-risk accounts.
- Utilizing YARA rules to detect malicious PDF files containing phishing URLs.
YARA Rules and Indicators of Compromise (IOCs)
To aid in detection, EclecticIQ provides YARA rules for identifying malicious PDFs and phishing domains associated with ONNX Store. Notable IOCs include:
- Phishing URLs: authmicronlineonfication[.]com, verify-office-outlook[.]com
- Malicious PDF File Hashes: 432b1b688e21e43d2ccc68e040b3ecac4734b7d1d4356049f9e1297814627cb3
MITRE ATT&CK Techniques
The following MITRE ATT&CK techniques are associated with ONNX Store’s operations:
- T1566.001 – Spearphishing Attachment
- T1204 – User Execution
- T1539 – Steal Web Session Cookie
- T1567 – Exfiltration Over Web Service
- T1132.001 – Data Encoding: Standard Encoding
- T1027 – Obfuscated Files or Information
- T1090.004 – Proxy: Domain Fronting
- T1114 – Email Collection
- T1557 – Adversary-in-the-Middle
Conclusion
ONNX Store represents a significant threat to Microsoft 365 account holders, especially in the financial services sector. Its advanced phishing capabilities and robust infrastructure make it a formidable tool for cybercriminals. To protect against these sophisticated attacks, organizations must adopt stringent cybersecurity measures and remain vigilant against emerging phishing techniques.
Our cybersecurity firm is here to provide expert guidance and tailored solutions to safeguard your organization against evolving cyber threats.

