In the year 2023, a total of 26,447 vulnerabilities were disclosed, marking an increase of over 1500 from the preceding year. This information is derived from the most recent report by the Qualys Threat Research Unit (TRU), released recently. Notably, less than 1% of these vulnerabilities are considered high-risk and are actively exploited by ransomware, threat actors, and malware. To provide perspective, 97 high-risk vulnerabilities—those with a high likelihood of exploitation—were absent from the CISA Known Exploited Vulnerabilities catalog. Furthermore, an alarming 25% of these high-risk vulnerabilities were exploited on the very day of their discovery.
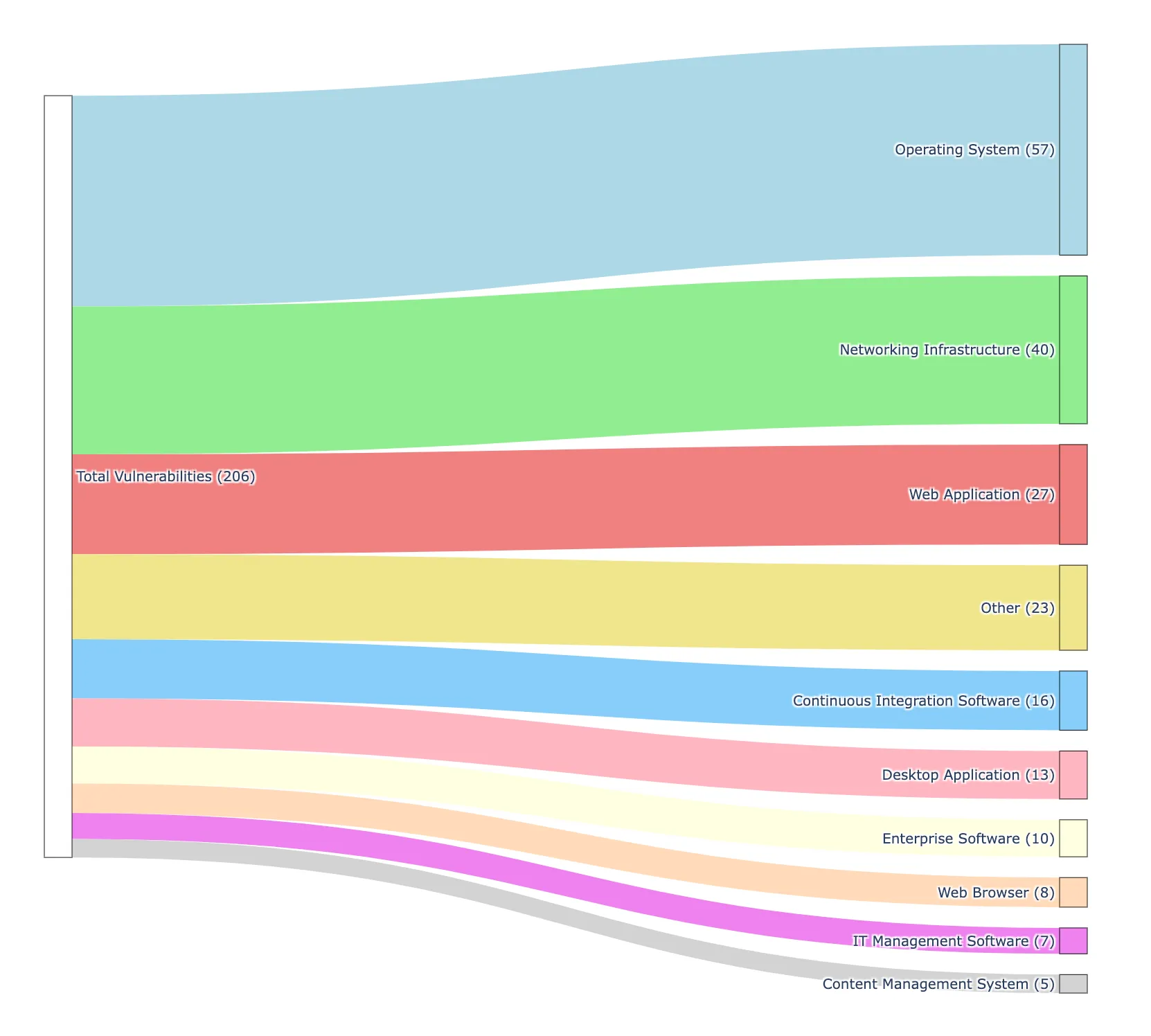
Delving deeper into the vulnerability landscape, it is revealed that over 7000 vulnerabilities had proof-of-concept exploit code, while 206 were equipped with weaponized exploit code, significantly elevating the potential for successful cyber compromises. Among the high-risk vulnerabilities, 32.5% are found to target network devices and web applications, underscoring the necessity for a robust vulnerability management strategy.
Credit Qualys Threat Research Unit
The Qualys TRU also provided insight into the mean time required to exploit high-risk vulnerabilities in 2023, averaging at 44 days. From a technical perspective, the predominant MITRE ATT&CK tactics and techniques used in exploits involve the exploitation of remote services, public-facing applications, and privilege escalation. Highlighting specific vulnerabilities, CVE-2023-27350 in PaperCut NG and CVE-2023-0669 in Fortra GoAnywhere MFT have emerged as notable targets in the digital attack landscape.
Behind the scenes, threat actors such as TA505 (also known as the Cl0p Ransomware Gang) and malware entities like LockBit and Clop have played substantial roles in prominent cyber-attacks, leveraging zero-day vulnerabilities and accentuating the critical need for enhanced cybersecurity measures. As organizations contend with the dynamic nature of cyber threats, the Qualys TRU recommends a pragmatic approach to vulnerability prioritization. This involves focusing on known exploits in the wild, those with a high likelihood of exploitation, and those armed with weaponized exploit code. John Gallagher, VP of Viakoo Labs at Viakoo, emphasizes the urgency, stressing that organizations must enhance their strategies for threat mitigation and remediation. With threats proliferating rapidly, the role of automation becomes paramount in reducing the mean time to exploitation.
The suggested action plan includes implementing effective network segmentation, automating patching and password rotation across device fleets, and extending zero trust principles to encompass all network-connected systems. This isn’t mere advice; it constitutes the comprehensive strategy for cybersecurity resilience in the ever-evolving digital landscape.
About Purple Shield Security
Purple Shield Security is not your typical cybersecurity consulting firm. We are the guardians of your digital realm, committed to protecting your business from the constantly evolving landscape of cyber threats. With a dedicated team of passionate security professionals by your side, we go above and beyond mere data and system protection – we provide you with peace of mind. Our comprehensive range of services includes Managed Cybersecurity Services, Security Assessments, Penetration Testing, Incident Response, and more. By harnessing cutting-edge solutions and leveraging our expertise, we empower you to fortify your web applications and minimize vulnerability to attacks.
Don’t wait to secure your business. Get in touch with us today and discover how Purple Shield Security can revolutionize your cybersecurity defenses.
#cybersecuritynews #securitynews #hacking #datasecurity #cyberprotection #ransomware #vulnerability #Vulnerabilitymanagement