Microsoft has recently unveiled a new North Korean state-aligned threat actor named Moonstone Sleet, previously known as Storm-1789. This group is implicated in a series of sophisticated cyber attacks, blending traditional techniques with innovative methodologies to target various sectors, including software, IT, education, and defense. Moonstone Sleet’s operations highlight the evolving landscape of cyber threats and the persistent danger posed by North Korean cyber actors.
The Emergence and Tactics of Moonstone Sleet
Moonstone Sleet has demonstrated significant overlaps with other North Korean threat actors, notably the infamous Lazarus Group, also known as Diamond Sleet. Initially, Moonstone Sleet extensively reused code from Lazarus’s known malware, such as Comebacker. However, it quickly developed its unique infrastructure and attack methods, distinguishing itself from its predecessors.
Key Tactics, Techniques, and Procedures (TTPs):
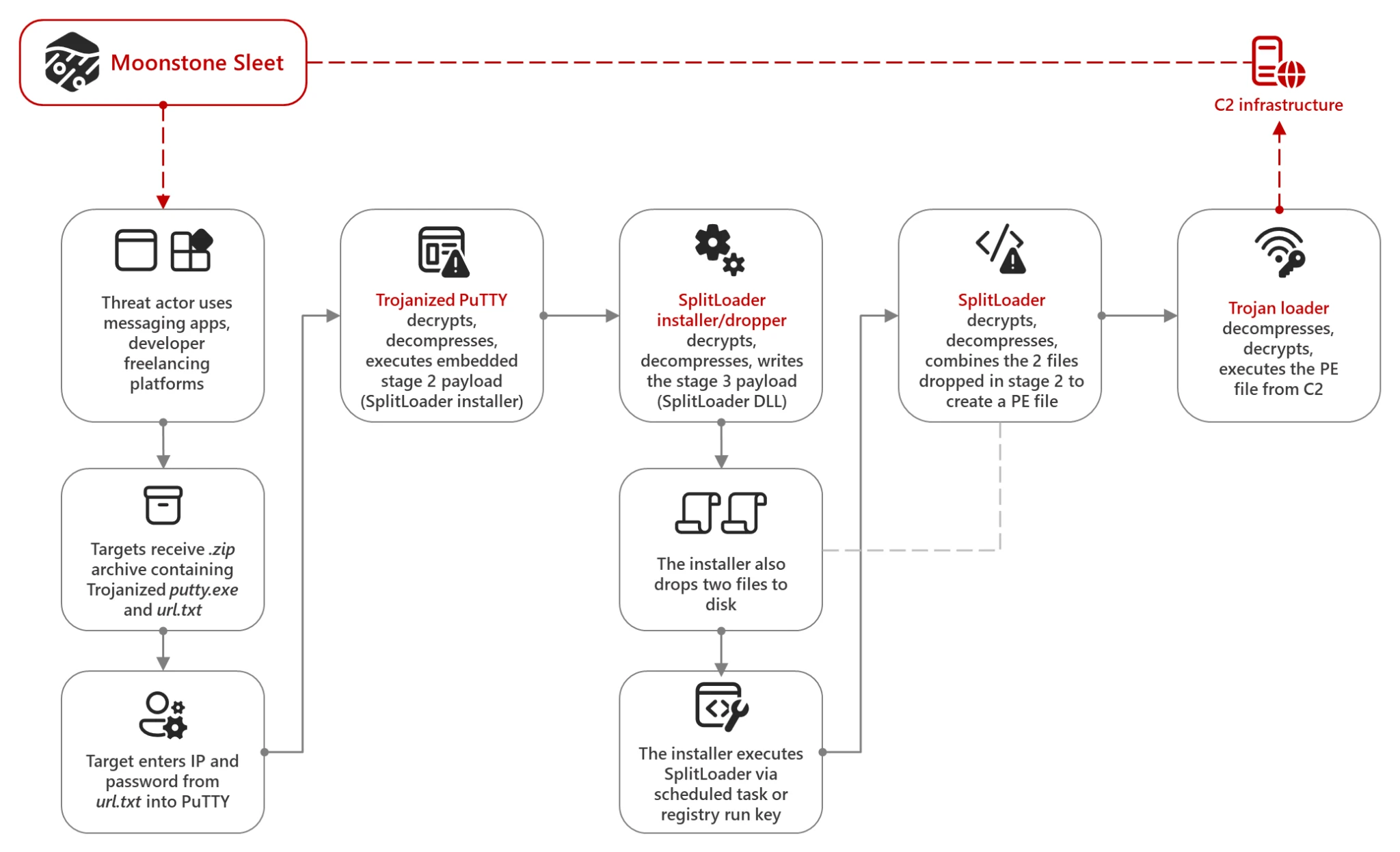
- Trojanized Software: Moonstone Sleet has employed trojanized versions of legitimate tools like PuTTY, distributed via LinkedIn, Telegram, and freelancing platforms. This tactic mirrors previous methods used by Lazarus in campaigns such as Operation Dream Job. The malicious PuTTY executable is designed to drop a custom installer dubbed SplitLoader, which initiates a sequence of intermediate stages to ultimately launch a Trojan loader that executes additional payloads from a command-and-control (C2) server.
- Malicious npm Packages: The group has used malicious npm packages to deliver payloads, including info-stealers. These packages are often shared through fake companies or job offers, targeting software developers. For instance, npm packages delivered through LinkedIn or freelancing websites often masquerade as technical skills assessments, connecting to actor-controlled IP addresses and dropping payloads similar to SplitLoader or facilitating credential theft from the Windows Local Security Authority Subsystem Service (LSASS).
- Fake Companies: Moonstone Sleet has set up several fake software development and IT consulting firms, such as C.C. Waterfall and StarGlow Ventures, to lure victims. These entities create a facade of legitimacy through well-crafted websites, fake employee personas, and social media presence. The group has used these fake companies to approach targets through messaging platforms or emails, presenting themselves as legitimate businesses seeking investment or developer support.
- Custom Malware and Ransomware: One of the group’s notable innovations is the deployment of a custom ransomware variant named FakePenny, demanding ransoms up to $6.6 million in Bitcoin. Additionally, they have developed bespoke malware loaders like YouieLoad, capable of sophisticated network and user data collection. YouieLoad, for instance, is used to load next-stage payloads in memory and create malicious services for network and user discovery and browser data collection.
Notable Incidents and Operations
Moonstone Sleet’s operations have been varied and impactful. Here are some of the critical incidents:
- FakePenny Ransomware: In April 2024, Moonstone Sleet deployed FakePenny against a defense technology company, demanding a $6.6 million ransom. This incident underscores the group’s shift towards financially motivated attacks alongside traditional cyber espionage. Unlike previous ransomware attacks coordinated by North Korean state hackers, which demanded $100,000, the significant ransom demanded by Moonstone Sleet highlights their aggressive financial extortion strategies.
- DeTankWar Game: In another campaign, the group distributed a malicious game named DeTankWar through emails and messaging platforms, pretending to be a blockchain-related project. This game contained YouieLoad, a loader that delivers next-stage payloads and collects sensitive data. The group masqueraded as a legitimate blockchain company or created fake companies like C.C. Waterfall to contact targets, presenting the game as a collaborative opportunity.
- Employment Scams: Moonstone Sleet has also targeted legitimate companies by attempting to get employed as software developers. This approach could facilitate access to sensitive systems and information, potentially leading to software supply chain attacks. This activity is consistent with previous reports from the United States Department of Justice that North Korea uses highly skilled remote IT workers to generate revenue or gain covert access to organizations.
Strategic Objectives and Evolution
The strategic objectives of Moonstone Sleet are multifaceted, encompassing revenue generation, intelligence gathering, and disruption of adversaries. The group’s ability to adapt and evolve its tactics from those used by other North Korean actors highlights its resilience and resourcefulness.
Evolution of Tactics:
- From Lazarus to Moonstone Sleet: nitially mirroring Lazarus Group’s techniques, Moonstone Sleet has progressively developed its bespoke tools and infrastructure. This evolution reflects a broader trend among North Korean cyber groups to diversify their capabilities and enhance their operational security. The similarities with Lazarus include extensively reusing code from known malware such as Comebacker, first observed in January 2021 in connection with campaigns targeting security researchers working on vulnerability research and development.
- Integration of Ransomware: The inclusion of ransomware in Moonstone Sleet’s arsenal indicates a shift towards more aggressive financial extortion methods, likely driven by the need to circumvent international sanctions and generate illicit revenue. This tactic is pulled straight out of the playbook of Andariel (aka Onyx Sleet), another North Korean threat actor known for ransomware families like H0lyGh0st and Maui.
Recommendations and Mitigations
Microsoft and other cybersecurity experts have provided several recommendations to mitigate the threat posed by Moonstone Sleet:
- Enhanced Awareness: Organizations, especially those in targeted sectors, should stay alert and knowledgeable about the group’s tactics. Implementing robust cybersecurity measures and keeping up with the latest threat intelligence is essential.
- Indicators of Compromise (IOCs): Microsoft has shared IOCs and hunting queries to help organizations detect and respond to Moonstone Sleet’s activities. These include specific patterns of network traffic, file hashes, and behavioral indicators that can reveal the presence of Moonstone Sleet’s malware.
- Supply Chain Security: Given the group’s propensity for targeting software supply chains, companies should scrutinize their development processes and third-party dependencies to prevent malicious infiltrations. Implementing strict code review practices, using signed code, and regularly auditing dependencies can help safeguard against supply chain attacks.
Conclusion
Moonstone Sleet represents a significant and evolving threat in the cybersecurity landscape. By blending traditional North Korean cyber tactics with innovative strategies and bespoke malware, the group exemplifies the persistent and adaptive nature of state-sponsored cyber espionage and financial crime. Organizations must remain proactive and resilient to defend against such sophisticated adversaries.
Understanding and addressing the tactics and strategies employed by Moonstone Sleet will better prepare us for future cyber threats and help safeguard critical information and infrastructure from relentless adversaries. This ongoing awareness and adaptability are essential in maintaining a robust cybersecurity posture in the face of evolving global threats.