As digital transformation accelerates, the sophistication of cyber threats has also increased. Recent discoveries by Check Point Research have brought to light a significant vulnerability in Foxit PDF Reader, a popular software used by over 700 million users worldwide. This flaw has been exploited by threat actors to deliver malware via booby-trapped PDF documents.
Overview of the Exploit
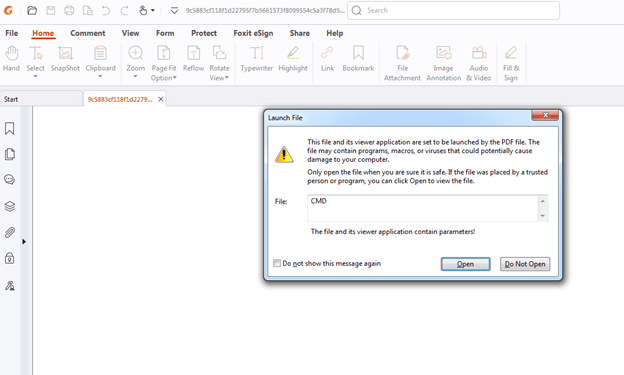
The primary issue lies in the flawed design of Foxit PDF Reader’s security alerts. When users open a manipulated PDF file, they are prompted with security warnings that, if ignored, can lead to the execution of harmful commands. Researchers have identified that these alerts often present the most dangerous option as the default, increasing the likelihood of users inadvertently allowing malicious actions.
Details of the Exploit
- Triggering Security Warnings: The exploit leverages the design of Foxit Reader’s warning messages. When a user opens an altered PDF, a security warning is triggered. If the user proceeds with the default options—typically the most harmful—the exploit downloads and executes a payload from a remote server.
- Exploit Builders: Various .NET and Python exploit builders, such as the “PDF Exploit Builder,” are used to create these malicious PDF documents. These builders insert placeholder text into the PDF template, which is replaced with a URL to download the malicious file once the user provides input.
- Attack Chain: Attackers use these booby-trapped PDFs to execute commands or scripts that download and install malware like Agent Tesla, Remcos RAT, Xworm, NanoCore RAT, and others. This exploit has been used in various malicious campaigns, including espionage and e-crime, by different threat actors, including the APT-C-35/DoNot Team, which has targeted both Windows and Android devices, bypassing Two-Factor Authentication (2FA).
The infection success and low detection rates allow these malicious PDFs to be distributed via unconventional channels, such as social media platforms like Facebook. Researchers followed a campaign where malicious links distributed via Facebook resulted in a long attack chain, eventually dropping an info stealer and two crypto miners. Another campaign utilized chained PDF files hosted on legitimate websites like Trello.
Foxit has acknowledged the issue and plans to resolve it in version 2024.3. Users are advised to exercise caution when opening PDF files from unknown sources. The recommended mitigation strategy includes disabling the execution of command-line instructions through PDF files or ensuring that the default options in security alerts do not inadvertently enable harmful actions.
The exploitation of Foxit PDF Reader’s design flaws highlights the need for heightened awareness among users and organizations. As threat actors continue to evolve their tactics, leveraging sophisticated tools and social engineering techniques, it is crucial to stay informed about potential vulnerabilities and adopt best practices for cybersecurity. Ensuring software is up-to-date and exercising caution with unsolicited files can significantly mitigate the risks associated with such exploits.