In a new research, SafeBreach’s Or Yair has unveiled significant security vulnerabilities in the Windows DOS-to-NT path conversion process. These findings, which Yair presented at the Black Hat Asia conference, illustrate how attackers could potentially achieve rootkit-like capabilities without requiring administrative permissions.
Understanding the DOS-to-NT Path Conversion Vulnerability
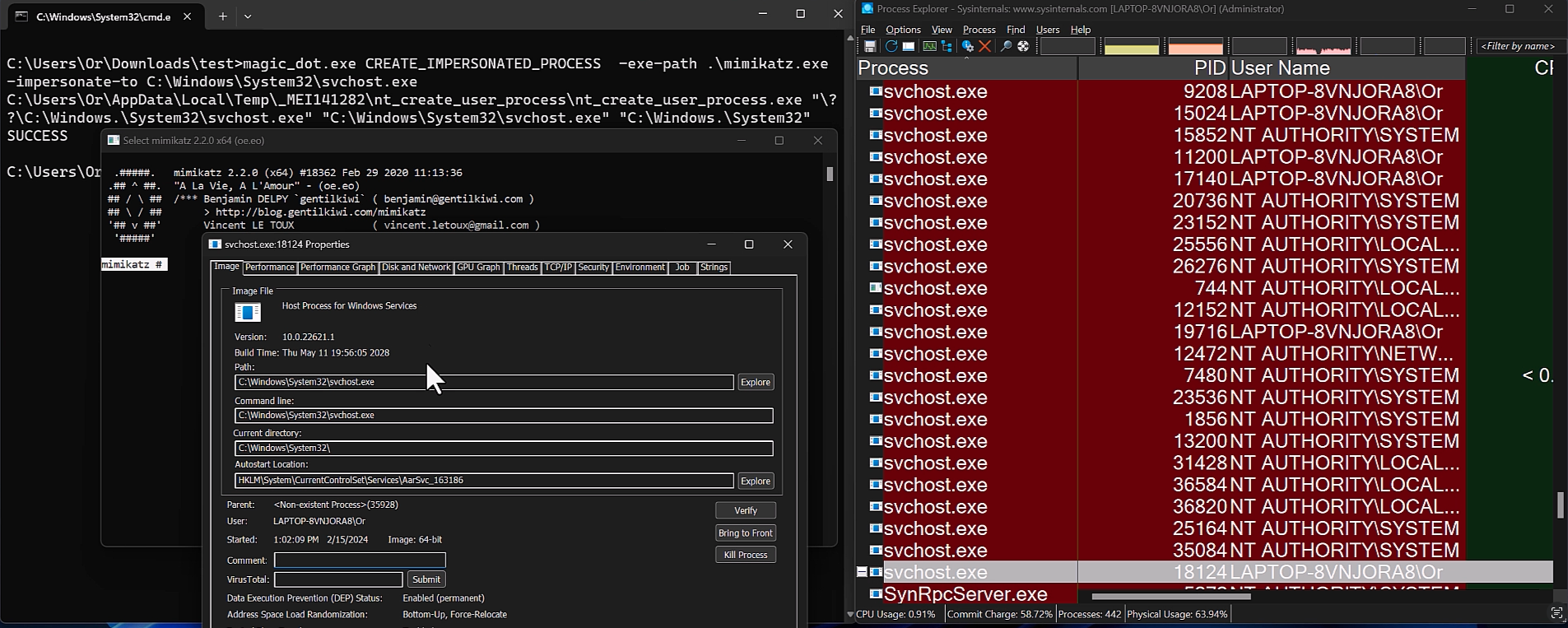
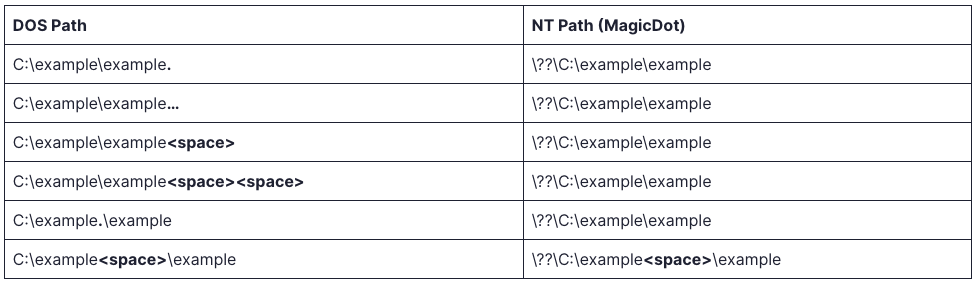
During a typical operation where a Windows function requires a path, the system converts DOS paths to NT paths. This conversion is crucial for file and directory management. However, Yair discovered that during this process, certain path manipulations—specifically, the removal of trailing dots and spaces—could be exploited to create severe security lapses.
Detailed Breakdown of Key Vulnerabilities
- Remote Code Execution (CVE-2023-36396, CVSS: 7.8):
- Vulnerability: This flaw resides in Windows’s handling of archive extraction. Attackers could craft a malicious archive that, once extracted, allows them to execute arbitrary code on a remote machine.
- Impact: Provides attackers the capability to control affected systems remotely, potentially leading to data theft, system corruption, or further network infiltration.
- Elevation of Privilege (Write) (CVE-2023-32054, CVSS: 7.3):
- Vulnerability: Exploits the Volume Shadow Copy service by manipulating the restoration process, allowing unauthorized modification of files.
- Impact: Enables attackers to alter or corrupt system files, which could lead to system instability or be used to install further malicious payloads.
- Denial of Service (DoS) (CVE-2023-42757):
- Vulnerability: Involves Process Explorer being disrupted by launching a process whose executable name is excessively long and lacks a file extension.
- Impact: Disrupts system monitoring tools, potentially hiding malicious activities or causing system instability.
- Elevation of Privilege (Deletion):
- Vulnerability: Allows deletion of files without the necessary permissions. Not yet fixed or assigned a CVE.
- Impact: Could be used to remove critical system files or logs, aiding attackers in covering their tracks or crippling system functionalities.
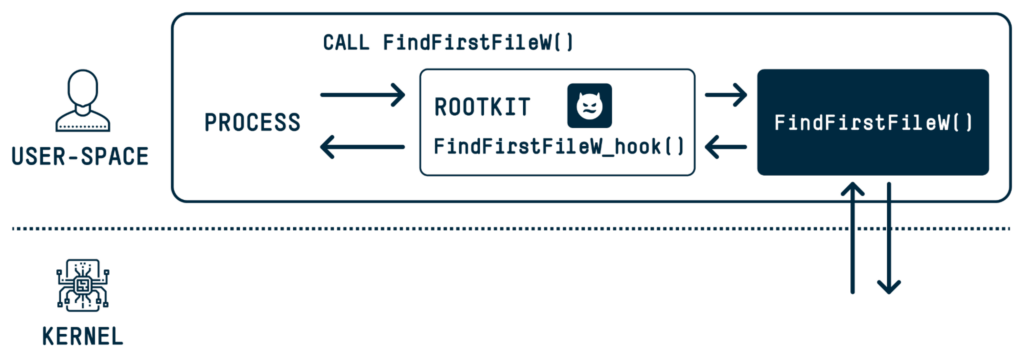
Exploitation Techniques and Rootkit Capabilities
Using what Yair terms “MagicDot” paths, unprivileged users can gain functionalities akin to those of rootkits:
- Concealment of malicious files and processes, making them invisible to both users and system monitoring tools.
- Deception by making malicious files appear as verified executables from Microsoft, misleading end-users and bypassing security checks.
- Disruption of system tools like Task Manager and Process Explorer, further aiding in maintaining the stealth of malicious operations.
Industry Implications
These vulnerabilities illustrate a critical need for readiness and regular updates in software systems, particularly those as widely utilized as Microsoft Windows. Yair’s research emphasizes the potential for “minor” bugs to evolve into significant threats, affecting millions of users globally.
Microsoft’s Response
The Microsoft Security Response Center (MSRC) has acknowledged these vulnerabilities, with some already addressed. The remaining are slated for future updates, emphasizing ongoing efforts to enhance cybersecurity.