Introduction to Compliance and Cybersecurity
In today’s digital landscape, the importance of compliance within the realm of cybersecurity cannot be overstated. For businesses, both large and small, adhering to compliance standards is not merely a matter of legal or regulatory obligation; it’s a cornerstone of trust, security, and integrity in operations. Compliance is intricately woven into the fabric of governance, risk management, and compliance (GRC) strategies, serving as a guiding force that shapes the approach to managing and mitigating risks effectively.
The role of security teams in this context is fundamentally transformative. Far from being peripheral players, they are central to developing, implementing, and maintaining an organization’s compliance and security framework. Their expertise and actions directly influence the organization’s ability to safeguard sensitive data, maintain customer trust, and navigate the complex landscape of regulatory requirements.
With the introduction of the Payment Card Industry Data Security Standard (PCI DSS 4.0), the concept of compliance undergoes a significant evolution. This latest version of the standard is not just an update; it’s a redefinition of what compliance means in the context of contemporary cybersecurity challenges. PCI DSS 4.0 reflects a holistic view of security, emphasizing proactive risk management, advanced threat protection, and a culture of continuous improvement.
Evolution of PCI DSS Towards Enhanced Security
The shift from mere compliance checklists to embedding best security practices marks the evolution of PCI DSS standards. The introduction of PCI DSS 4.0 sets new benchmarks for businesses processing credit card transactions, demanding adherence to stringent security measures.
Understanding PCI DSS and Its Impact
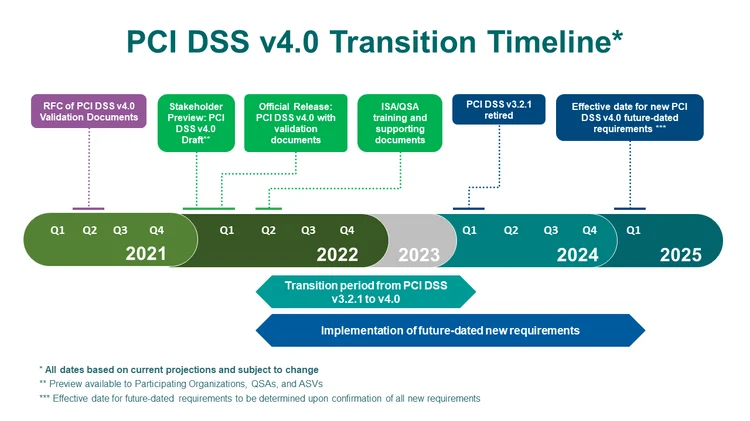
The PCI Security Standards Council (PCI SSC) mandates compliance with PCI DSS standards for all merchants accepting credit card payments. The introduction of PCI DSS 4.0 in March 2022 marks a significant milestone in the evolution of these security standards. With this latest update, the PCI SSC has not only addressed new and emerging threats but also placed a stronger emphasis on adapting security practices to match the complexity of modern payment environments. The two-year transition period set forth by the PCI SSC is a clear indication of the urgency and importance placed on compliance with the updated standards. This transitional window is designed to give businesses adequate time to understand the new requirements, assess their current security posture, and implement necessary changes without disrupting their operations.
In-Depth Look at PCI DSS 4.0 Enhancements
- Combatting Malicious Scripts: The first line of defense involves implementing robust protective controls that prevent the insertion of malicious scripts into payment pages. This proactive approach requires businesses to rigorously evaluate and monitor all third-party services and scripts integrated into their payment processing systems. It’s about creating a secure baseline where only authorized and verified scripts are allowed to run. Techniques such as Content Security Policy (CSP) can be effective in preventing unauthorized script execution, thereby reducing the risk of skimming attacks.
- Detective Controls for Ongoing Monitoring: Complementing protective measures, detective controls play a critical role in identifying and responding to threats that may bypass initial defenses. Continuous monitoring of payment pages for unauthorized script modifications is vital. By employing real-time detection tools and anomaly detection algorithms, businesses can quickly identify suspicious activities indicative of skimming attempts. Once detected, immediate alerts enable swift response actions to mitigate potential damage. These detective measures are not only about detecting attacks as they happen but also about understanding attack patterns, which can inform future security enhancements. Regularly scanning payment environments for vulnerabilities and unauthorized changes forms a crucial part of maintaining a secure payment processing ecosystem.
- Enhancing Company Defense Against Skimming Attacks: The combination of protective and detective controls as mandated by PCI DSS 4.0 significantly fortifies a company’s defenses against skimming attacks. By implementing these controls, businesses can protect their customers’ sensitive information, preserve customer trust, and comply with industry-leading data security standards.
Moreover, beyond compliance, these measures represent a commitment to maintaining a secure and trustworthy payment environment. They require ongoing effort and vigilance but offer substantial returns in the form of enhanced security, reduced fraud, and the mitigation of financial and reputational risks associated with data breaches.
- Understanding Modern Network Environments: Today’s network environments are characterized by their diversity and complexity. Businesses often operate across a blend of traditional on-premises data centers, public and private clouds, and multicloud environments. Each of these setups presents unique security challenges and vulnerabilities, from the sprawl of endpoints to the intricacies of cloud access and data sovereignty issues.
- Strategizing for Comprehensive Network Security: In response to this complexity, PCI DSS 4.0 encourages businesses to adopt a strategic approach to network security that is as dynamic as the environments they operate in. This includes:
- Implementing Advanced Network Security Controls: Beyond traditional firewalls and intrusion detection systems, organizations are urged to deploy advanced security solutions. These can include next-generation firewalls, cloud access security brokers (CASBs), and solutions for secure access service edge (SASE), which combine network security functions with wide-area networking capabilities to support the dynamic, secure access needs of today’s distributed enterprises.
- Embracing Zero Trust Architecture: Adopting a zero-trust framework, where trust is never assumed and verification is required from everyone trying to access resources in the network, is becoming a cornerstone of modern network security strategies. This approach minimizes the attack surface and reduces the impact of potential breaches.
- Securing Multicloud Environments: With many businesses leveraging multicloud strategies to avoid vendor lock-in and optimize performance, securing these environments is crucial. This involves ensuring consistent security policies across all cloud platforms, employing end-to-end encryption, and utilizing cloud-native security features offered by cloud service providers.
- Continuous Monitoring and Threat Detection: Continuous monitoring of network traffic and user behaviors across all environments helps in the early detection of potential threats. Employing security information and event management (SIEM) systems, network detection and response (NDR) tools, and advanced analytics can provide real-time insight into security threats, enabling swift response.
- Emphasizing Secure Development Practices: Secure development practices are crucial for creating software that is resilient to cyber threats from the ground up. This involves incorporating security considerations into every stage of the software development lifecycle (SDLC), from planning and design to implementation, testing, and maintenance.
- Strengthening API Security: As the conduits through which different software systems communicate, APIs represent critical points of vulnerability if not properly secured. Effective API management and security measures are thus essential components of modern cybersecurity frameworks.
- Managing Unregistered APIs: A significant challenge in API security is the detection and management of unregistered or “shadow” APIs, which can be created inadvertently or deliberately bypass official development processes. Unregistered APIs can expose organizations to significant security risks, as they often lack the rigorous security controls of their sanctioned counterparts.
- Enhancing Logging, Visibility, and Monitoring: Robust logging and monitoring are essential for understanding and mitigating security incidents. PCI DSS 4.0 emphasizes the need for extensive visibility across operational environments, promoting proactive monitoring and response strategies to ensure compliance and security.
- Achieving Extensive Visibility: Visibility, in the context of PCI DSS 4.0, means having a clear, uninterrupted view into all aspects of the IT environment, including on-premises systems, cloud services, and remote endpoints.
- Real-time Analysis: Employing security information and event management (SIEM) systems for real-time analysis of log data helps identify patterns that could indicate a cybersecurity threat.
- Automated Alerts: Setting up automated alerts based on specific indicators of compromise (IoCs) or unusual activity patterns ensures that potential threats are promptly identified and escalated.
- Incident Response Integration: The monitoring system should be integrated with the organization’s incident response plan, enabling automatic or semi-automatic response mechanisms to contain and mitigate threats as they are detected.
Conclusion: Broader Implications for Business Security
The advancements in PCI DSS 4.0 extend beyond payment security, offering a blueprint for strengthening the overall security posture of businesses. By aligning with these updated standards, organizations can not only ensure compliance but also enhance their resilience against a wide range of cyber threats.
About Purple Shield Security
Purple Shield Security isn’t just another cyber security firm. Think of us as your digital world’s protectors, always ready to keep your business safe from the latest cyber threats. Our team is full of passionate experts who do more than just look after your data and systems; we give you peace of mind. We offer a wide range of services like Managed Cyber Security, Cyber Security Consulting, Cyber Security Risk Analysis, Cyber Defense Services, Cyber Security Incident Response, and vCISO.
Don’t put off making your business safer. Contact us now to see how Purple Shield Security can upgrade your cyber defenses.