A new report highlights innovative ways that cyber threats can exploit vulnerabilities in Google Workspace and the Google Cloud Platform. These methods, if exploited by malicious actors, could lead to ransomware attacks, data theft, and password recovery breaches.
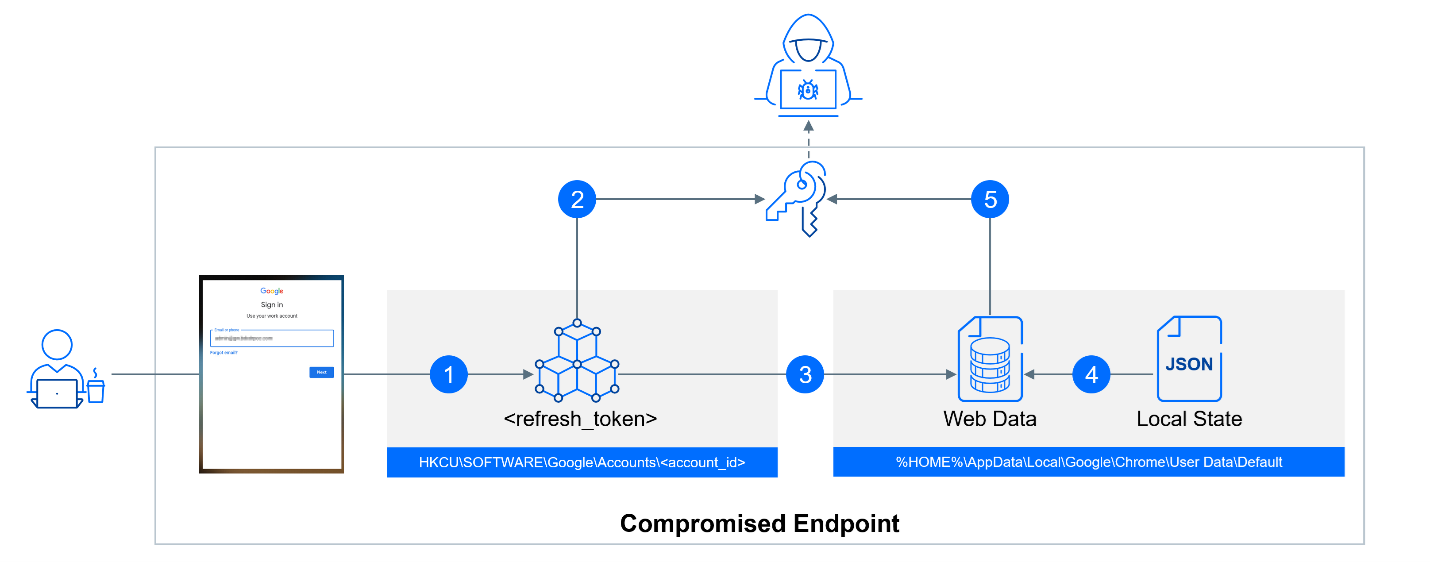
According to Martin Zugec, the Technical Solutions Director at Bitdefender, the threat begins with compromising a single machine. From there, attackers could take various routes, such as moving to other machines with Google Credential Provider for Windows (GCPW) installed, gaining access to the cloud platform with customized permissions, or decrypting locally stored passwords. Zugec emphasizes that these attacks go beyond Google’s usual threat model and align with Chrome’s local data storage practices. Bitdefender warns that even though Google does not consider this a fixable bug, threat actors can exploit these vulnerabilities to extend a compromise from a single endpoint to an entire network breach.
The attacks hinge on an organization’s use of Google Credential Provider for Windows (GCPW), which combines mobile device management (MDM) and single sign-on (SSO) capabilities. GCPW allows administrators to manage Windows devices within Google Workspace environments remotely. Users can access their Windows devices using the same credentials as their Google accounts. GCPW uses a local privileged service account called Google Accounts and ID Administration (GAIA) to streamline the sign-in process by connecting to Google APIs and storing a refresh token, eliminating the need for re-authentication. An attacker with access to a compromised machine can extract an account’s refresh OAuth tokens and bypass multi-factor authentication (MFA) protections, leading to potential unauthorized access.
The second exploit, known as Golden Image lateral movement, targets virtual machine (VM) deployments. Cloning a machine with pre-installed GCPW results in the cloning of the GAIA account password. If all machines share the same password for local accounts, knowing one password grants access to all machines.
The third attack involves accessing plaintext credentials by using the acquired access token to send a request to an undocumented API endpoint. This allows the attacker to obtain the private RSA key necessary to decrypt the password field. Zugec emphasizes that having access to plaintext credentials poses a significant threat, as it enables attackers to impersonate legitimate users, potentially leading to complete account takeover.
While the identified vulnerabilities present security risks, they emphasize the importance of local device security. Purple Shield Security recommends prioritizing detection and response capabilities, investing in advanced threat detection solutions, and developing an incident response plan to address security incidents effectively.
About Purple Shield Security
Purple Shield Security is not your typical cybersecurity consulting firm. We are the guardians of your digital realm, committed to protecting your business from the constantly evolving landscape of cyber threats. With a dedicated team of passionate security professionals by your side, we go above and beyond mere data and system protection – we provide you with peace of mind. Our comprehensive range of services includes Managed Cybersecurity Services, Security Assessments, Penetration Testing, Incident Response, and more. By harnessing cutting-edge solutions and leveraging our expertise, we empower you to fortify your web applications and minimize vulnerability to attacks.
Don’t wait to secure your business. Get in touch with us today and discover how Purple Shield Security can revolutionize your cybersecurity defenses.
#cybersecuritynews #securitynews #hacking #datasecurity #google #googleworksapce #cloudsecurity #applicationvulnerability

