Cybersecurity experts at Trend Micro have discovered a critical remote code execution (RCE) vulnerability, identified as CVE-2024-38112, within the Microsoft MHTML protocol handler. This vulnerability, dubbed ZDI-CAN-24433, was reported to Microsoft and later patched. However, the advanced persistent threat (APT) group Void Banshee actively exploited it.
Exploitation by Void Banshee
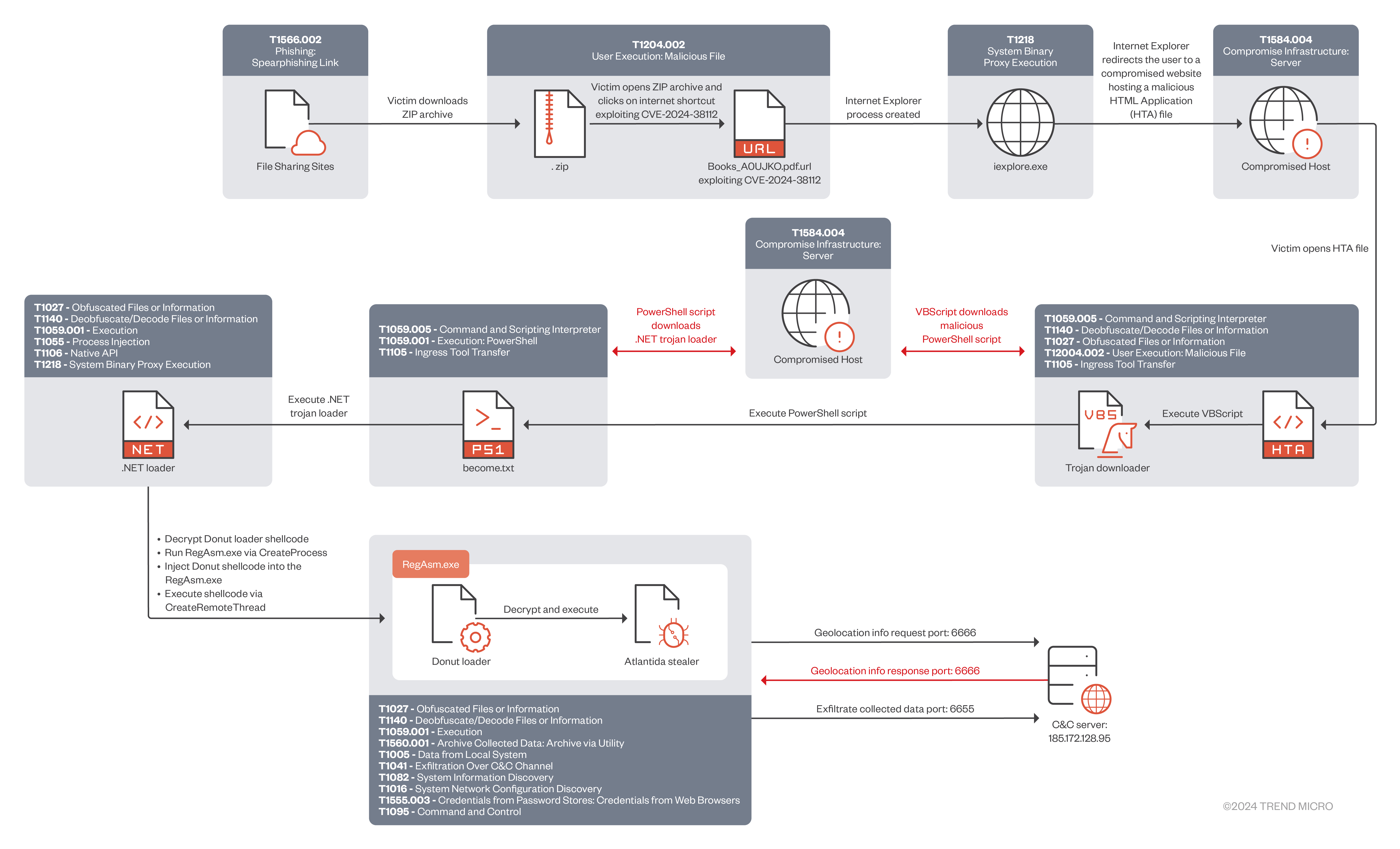
Void Banshee, known for targeting regions in North America, Europe, and Southeast Asia, leveraged CVE-2024-38112 as part of a sophisticated attack chain aimed at stealing sensitive information and achieving financial gain. The group used specially crafted internet shortcut (.URL) files to manipulate disabled instances of Internet Explorer on Windows systems, executing malicious payloads such as HTML Applications (HTA).
The attack concluded with the deployment of the Atlantida stealer, a type of malware that was first identified in January 2024. Throughout the year, variations of this campaign intensified, incorporating CVE-2024-38112 to compromise systems. Trend Micro monitored the evolving campaign in mid-May 2024, using internal and external telemetry to track Void Banshee’s tactics, techniques, and procedures (TTPs).
Detailed Attack Chain
The attackers used spear-phishing emails embedding links to ZIP archive files hosted on file-sharing sites. These archives contained URL files that exploited CVE-2024-38112, redirecting victims to compromised sites hosting malicious HTA files. Opening the HTA files executed a Visual Basic Script (VBS), which downloaded and ran a PowerShell script responsible for retrieving a .NET trojan loader. This loader ultimately used the Donut shellcode project to decrypt and execute the Atlantida stealer inside RegAsm.exe process memory.
Atlantida, modeled on open-source stealers like NecroStealer and PredatorTheStealer, extracts files, screenshots, geolocation data, and sensitive information from applications such as Telegram, Steam, FileZilla, and various cryptocurrency wallets. By using specially crafted URL files with the MHTML protocol handler and the x-usc! directive, Void Banshee could run HTML Application (HTA) files directly through the disabled IE process, similar to the exploitation method of CVE-2021-40444.
Response and Mitigation
Microsoft’s response to CVE-2024-38112 involved issuing a patch during the July 2024 Patch Tuesday cycle, which unregistered the MHTML handler from Internet Explorer, mitigating the risk posed by this vulnerability. Trend Micro’s report highlighted the ongoing concerns regarding the exploitation of legacy components like Internet Explorer, which, despite being phased out, remain latent vulnerabilities in modern Windows environments.
The severity of CVE-2024-38112 and its active exploitation underscore the need for organizations to adopt a proactive approach to cybersecurity. This includes advanced threat intelligence, constant monitoring, and scanning of software and network assets for potential flaws and attack surfaces.
Industry Concerns and Recommendations
The exploitation of CVE-2024-38112 demonstrates how unsupported and disabled system services, such as Internet Explorer, can still pose significant threats. Organizations must assume their systems are already compromised and work to isolate affected data or toolchains immediately.
To safeguard against similar threats, organizations should:
- Apply patches and updates promptly.
- Monitor for suspicious activities and potential indicators of compromise (IoCs).
- Engage in advanced threat intelligence and adopt a robust security posture.
- Educate employees about spear-phishing tactics and the risks of opening unfamiliar files.
By addressing these vulnerabilities and enhancing their cybersecurity measures, organizations can better protect themselves from sophisticated attacks like those carried out by Void Banshee.
For more details on the latest cybersecurity threats and protective measures, visit Microsoft Fixes Four Zero-Days in July Patch Tuesday.