Cybersecurity challenges have been a constant battle for organizations, including businesses, universities, and government agencies. Despite significant investments in security measures, data breaches have been on a relentless rise, with a notable 20% increase from 2022 to 2023. This surge has seen double the number of global victims and a 77% increase in ransomware activities in the Middle East within the same period. The persistence of these security breaches prompts the question: Why do they continue to escalate, and what proactive steps can we take?
Our research has identified three primary factors contributing to the rise in personal data theft: cloud misconfiguration, the evolution of ransomware attacks, and the exploitation of vendor systems. Addressing these areas offers a pathway to mitigating their impact.
Cloud Misconfiguration and Its Risks
Cloud storage, popularized by providers like Amazon, Google, and Microsoft, offers numerous benefits such as cost efficiency and scalability. Over 60% of global corporate data now resides in the cloud, making it an appealing target for cyberattacks. A staggering 80% of data breaches in 2023 involved cloud-stored data, largely due to misconfigurations.
Cloud misconfigurations arise from several factors. First, there’s the issue of complexity. Cloud services offer a vast array of settings and options, which can be daunting even for experienced IT professionals. The rapid pace of innovation in cloud services means that new features and functionalities are constantly being added, often without adequate guidance on secure implementation.
Then there’s the problem of default settings. Service providers, aiming to make their platforms as user-friendly as possible, often set defaults to the least restrictive access controls. While this approach facilitates ease of use and quick deployment, it can inadvertently leave systems exposed if the settings are not properly reviewed and adjusted.
The experience gap also plays a role. Many organizations migrating to the cloud do not have staff adequately trained to configure complex cloud environments securely. This lack of expertise leads to misconfigurations that can remain undetected until a breach occurs.
Ultimately, as the reliance on cloud storage continues to grow, so does the need for rigorous and proactive measures to secure it. Organizations that take the time to understand, implement, and regularly review their cloud security practices will be better positioned to enjoy the cloud’s benefits without falling prey to its associated risks.
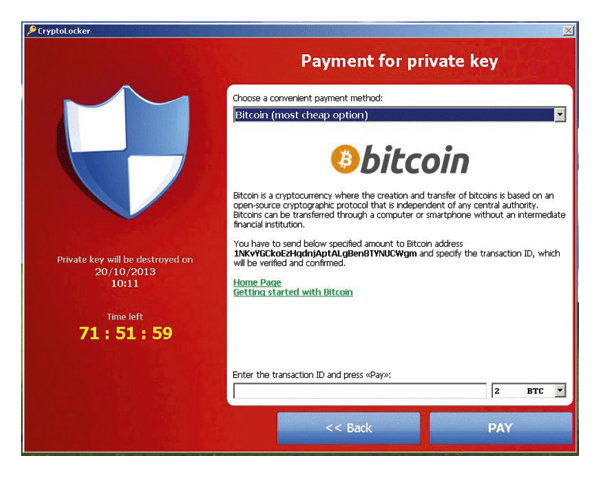
The New Wave of Ransomware Attacks
The Threat from Vendor Systems
To effectively counter the cybersecurity challenges highlighted—cloud misconfiguration, evolving ransomware attacks, and vendor system vulnerabilities—organizations must adopt a proactive, multifaceted security strategy. Here’s an advice and action plan tailored to address these issues:
1. Strengthen Cloud Security
- Conduct Regular Cybersecurity Risk Assessment: Implement routine security audits of your cloud environments to identify and rectify misconfigurations. Use automated tools that can scan for common misconfiguration issues.
- Adopt a Principle of Least Privilege (PoLP): Ensure access controls are strictly enforced, granting only necessary permissions to users and services.
- Implement Strong Authentication and Encryption: Use multi-factor authentication (MFA) for accessing cloud services and encrypt sensitive data both at rest and in transit.
2. Mitigate Ransomware Threats
- Comprehensive Backup Strategy: Maintain regular, encrypted backups of critical data in separate locations (offline or in a different cloud environment) to ensure you can restore information without paying a ransom.
- Educate Employees: Conduct regular training sessions on identifying phishing attempts and other common entry points for ransomware.
- Update and Patch Systems: Keep all systems and software up to date to protect against vulnerabilities that ransomware could exploit.
- Endpoint Protection: Deploy advanced endpoint security solutions that can detect, isolate, and neutralize ransomware attacks.
3. Secure Vendor Relationships
- Conduct Vendor Risk Assessments: Before engaging with new vendors, assess their security practices and policies. Consider third-party cybersecurity assessments or certifications as part of your evaluation.
- Limit Vendor Access: Only provide vendors with access to necessary systems and data. Use virtual private networks (VPNs), dedicated user accounts, and monitor their activities.
- Contractual Security Requirements: Include specific security requirements and responsibilities in contracts with vendors to ensure they adhere to your cybersecurity standards.
- Continuous Monitoring and Evaluation: Regularly review and monitor the security posture of your vendors to ensure compliance with security policies and practices.
- Incident Response Plan: Develop and regularly update an incident response plan to quickly address and mitigate any security breaches.
- Cybersecurity Insurance: Consider obtaining cybersecurity insurance to mitigate financial losses from cyber incidents.
- Stay Informed: Keep abreast of the latest cybersecurity trends, threats, and best practices by subscribing to reputable cybersecurity news sources and participating in industry forums.
4. Implement Security Information and Event Management (SIEM) Solutions
- Centralized Monitoring: Deploy SIEM technology to aggregate and analyze logs from across your systems, detecting anomalies and potential security incidents in real time. This centralized view is crucial for identifying and mitigating threats swiftly.
- Automated Response: Choose SIEM solutions that offer automated response capabilities, allowing you to quickly contain and mitigate threats without manual intervention.
5. Adopt Zero Trust Architecture
- Verify Explicitly: Operate under the principle that no entity, inside or outside the network, is trusted by default. Implement strict access controls and verification processes for every access request to resources, regardless of the source.
- Least-Privilege Access: Ensure that users and systems have access only to the resources necessary for their specific roles and functions, reducing the potential impact of a breach.
6. Implement Passwordless Authentication Technologies
- Enhance Security and User Experience: Adopt passwordless authentication methods, such as biometrics, security tokens, or mobile device authentication. These technologies not only improve security by eliminating the risks associated with weak or compromised passwords but also enhance user convenience.
7. Leverage Social Media and Web Monitoring
- Threat Intelligence: Use tools and services that monitor social media platforms and the dark web for mentions of your company or leaked data. This can provide early warnings about data breaches, phishing campaigns, or emerging threats targeting your organization.
8. Partner with a Cybersecurity Firm
- Engage Expertise: Collaborate with a reputable cybersecurity firm that can offer advanced threat intelligence, threats hunting, monitoring, vCISO services, and advanced defense services. This partnership can provide access to specialized skills and knowledge that may be beyond the internal capabilities of your organization.
Additional Considerations
- Regulatory Compliance: Ensure your cybersecurity practices comply with relevant laws and industry standards to protect not only your data but also to avoid legal penalties.
- Cybersecurity Framework Adoption: Consider adopting a recognized cybersecurity framework, such as NIST or ISO/IEC 27001, to guide your security efforts and ensure comprehensive coverage of potential vulnerabilities.
In conclusion, the escalation of cyberattacks underscores the need for a multifaceted approach to cybersecurity. Organizations must remain active against cloud misconfigurations, the evolving nature of ransomware, and the vulnerabilities within vendor systems. By integrating these additional strategies into your cybersecurity plan, you can create a robust defense posture that adapts to the evolving digital threat landscape. Partnering with security experts, leveraging cutting-edge technologies, and fostering a culture of security within your organization are key steps toward safeguarding your assets in an increasingly interconnected world.
About Purple Shield Security
Purple Shield Security is not your typical cyber security consulting firm. We are the guardians of your digital realm, committed to protecting your business from the constantly evolving landscape of cyber threats. With a dedicated team of passionate security professionals by your side, we go above and beyond mere data and system protection – we provide you with peace of mind. Our comprehensive range of services includes Managed Cybersecurity Services, Cyber Security Consulting, Cybersecurity Risk and Vulnerability Assessment, Cybersecurity Defense Services, Security Incident Response, CISO, and more. By harnessing cutting-edge solutions and leveraging our expertise, we empower you to fortify your IT infrastructure and minimize vulnerability to attacks.
Don’t wait to secure your business. Get in touch with us today and discover how Purple Shield Security can revolutionize your cybersecurity defenses.
