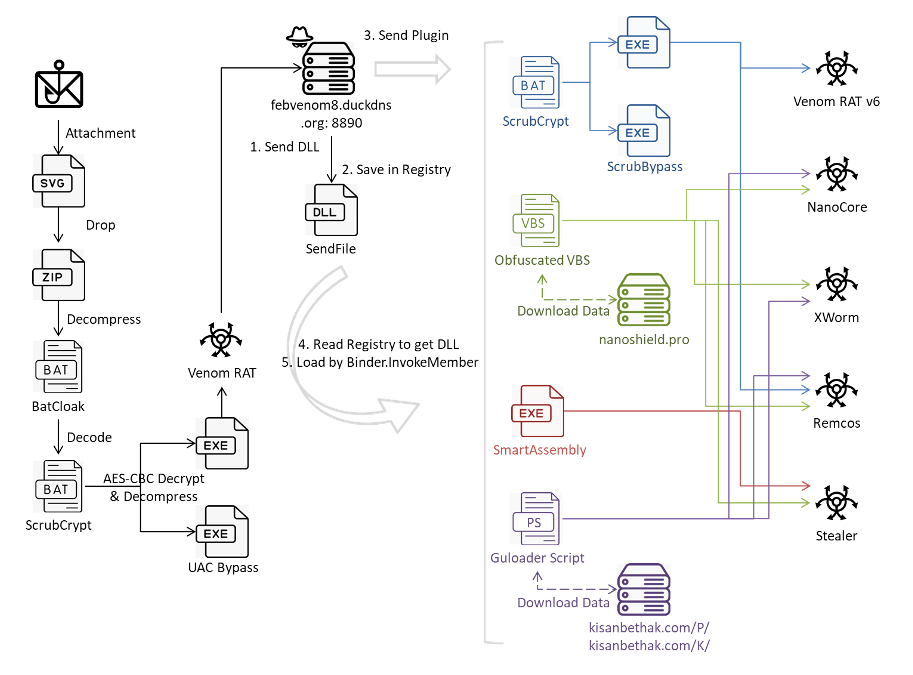
Cybersecurity researchers recently uncovered a complex multi-stage attack that targets users with invoice-themed phishing emails to deploy a variety of malware, including Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and a crypto wallet stealer. Attackers attach Scalable Vector Graphics (SVG) files to emails, which initiate the malware infection process upon opening, according to a technical report by Fortinet FortiGuard Labs.
This attack strategy stands out for its utilization of the BatCloak malware obfuscation engine and ScrubCrypt for delivering obfuscated batch scripts containing malware. Threat actors have had access to BatCloak, which builds on another tool called Jlaive, for sale since late 2022. Its main function is to load subsequent payloads while avoiding traditional detection methods.
ScrubCrypt, a crypter initially identified by Fortinet in March 2023 during a cryptojacking campaign by the 8220 Gang, emerges as a version of BatCloak, as per Trend Micro’s research from last year. In this new campaign, the cybersecurity firm discovered that the SVG file drops a ZIP archive containing a BatCloak-created batch script. This script then unpacks a ScrubCrypt batch file to execute Venom RAT, after ensuring persistence on the host and circumventing AMSI and ETW protections.
Venom RAT, a variant of Quasar RAT, enables attackers to take over compromised systems, collect sensitive data, and execute commands from a command-and-control (C2) server. Security researcher Cara Lin highlights that Venom RAT’s main function seems simple, but it maintains contact with the C2 server to download additional plugins for various operations, including versions with keylogger functions, NanoCore RAT, XWorm, and Remcos RAT.
Furthermore, the attackers deploy a plugin system to launch a stealer that captures system data and extracts information from various wallets and applications like Atomic Wallet, Electrum, Ethereum Exodus, Jaxx Liberty, Zcash, Foxmail, and Telegram, which it then transmits to an external server. Lin’s investigation underscores a complex attack that employs multiple obfuscation and evasion strategies to distribute and execute VenomRAT via ScrubCrypt. The attackers employ phishing emails with malicious SVG file attachments, obfuscated script files, and Guloader PowerShell as part of a versatile and adaptable campaign to penetrate and compromise systems.
About Purple Shield Security
Purple Shield Security stands out from the crowd of cyber security firms. Picture us as the guardians of your digital space, always on the lookout to protect your business from the newest cyber dangers. We’ve got a variety of services to help keep you safe, including Managed Cyber Security, Cyber Security Consulting, Risk Analysis, Defense Services, Incident Response, and even a virtual Chief Information Security Officer (vCISO).
Don’t put off making your business safer. Contact us now to see how Purple Shield Security can upgrade your cyber defenses.