Cybersecurity researchers at ThreatFabric have uncovered a macOS variant of the LightSpy spyware, previously known for targeting iOS and Android devices. This development highlights the extensive reach and sophistication of this surveillance tool. LightSpy, a modular framework, has evolved to infiltrate various platforms, posing significant threats to user privacy and security.
Origins and Evolution
First reported in 2020, LightSpy has been linked to an Android surveillance tool called DragonEgg. Subsequent investigations by ThreatFabric and Huntress Labs revealed its ability to target multiple platforms, including macOS, Windows, Linux, and even routers from manufacturers like NETGEAR, Linksys, and ASUS.
Exploitation Mechanism
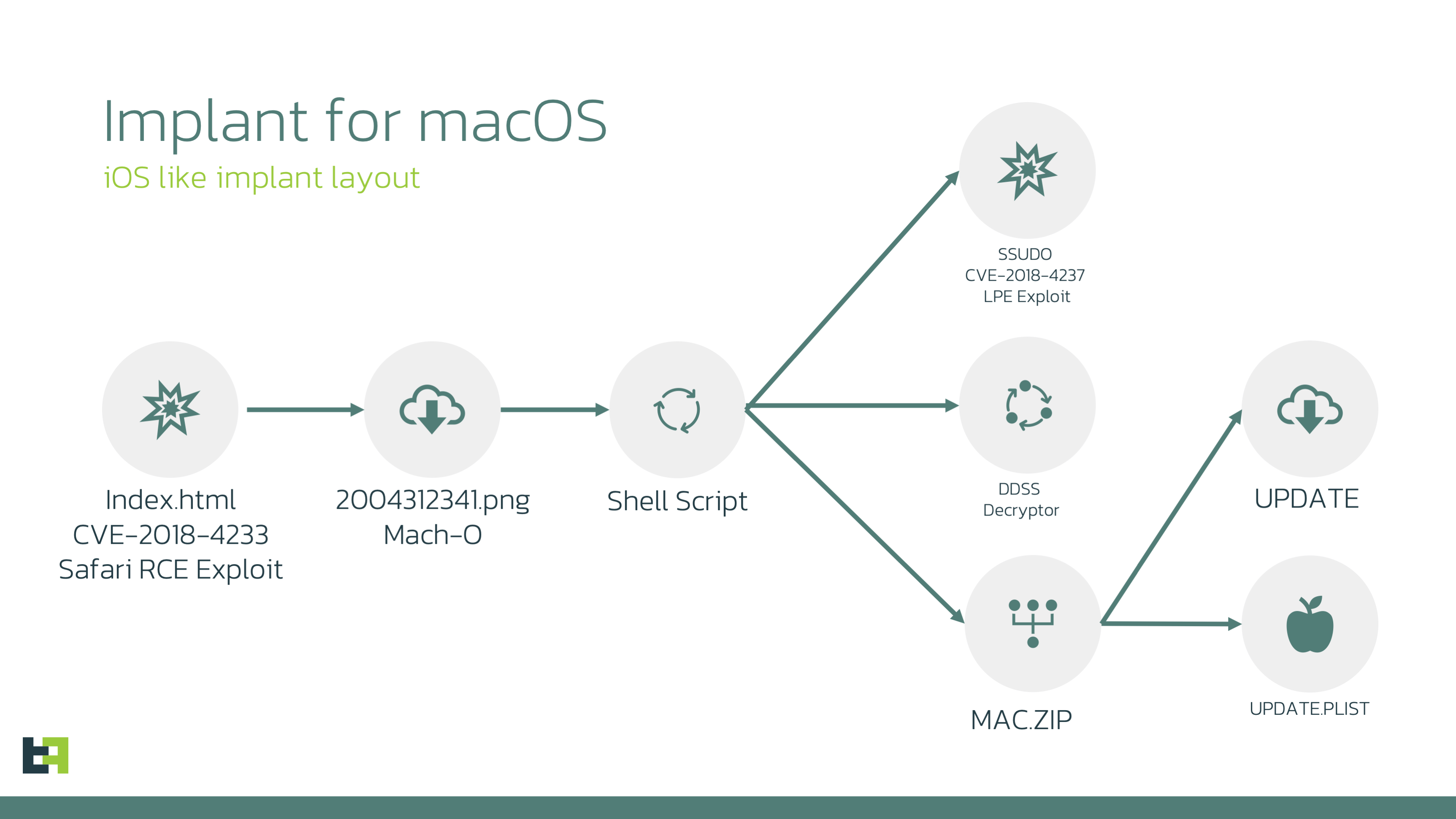
The macOS version of LightSpy employs publicly available exploits (CVE-2018-4233 and CVE-2018-4404) to deliver its payload. The attack chain starts with a Safari WebKit vulnerability that executes code, delivering a 64-bit MachO binary disguised as a PNG image. This binary decrypts and executes scripts that fetch additional payloads, including a privilege escalation exploit, an encryption utility, and a ZIP archive with further executables.
Functional Capabilities
LightSpy’s modular design allows it to perform various surveillance activities through plugins. The macOS version supports ten plugins, each designed to exfiltrate specific types of data:
- soundrecord: Captures audio from the microphone.
- browser: Extracts browsing data.
- cameramodule: Takes photos using the device’s camera.
- FileManage: Manages and exfiltrates files, especially from messaging apps.
- keychain: Retrieves sensitive information from the macOS Keychain.
- LanDevices: Gathers information about devices on the same local network.
- softlist: Lists installed applications and running processes.
- ScreenRecorder: Records screen activity.
- ShellCommand: Executes shell commands on the infected device.
- wifi: Collects data on Wi-Fi networks.
Discovery and Analysis
ThreatFabric’s analysis of LightSpy’s control panel revealed a misconfiguration that allowed unauthorized access. This enabled researchers to understand the spyware’s infrastructure, functionality, and the extent of infected devices. The panel showed that the macOS implant had been active since at least January 2024, primarily affecting test devices and a limited number of actual targets.
Impact and Implications
The macOS version’s discovery underscores LightSpy’s capability to infiltrate diverse systems. The spyware focuses on intercepting victim communications, including messenger conversations and voice recordings. A specialized plugin for macOS aims to identify nearby devices, indicating a broader surveillance strategy.
Conclusion
Despite these findings, some aspects of LightSpy remain unclear. As LightSpy continues to evolve, the need for robust cybersecurity services becomes increasingly critical.